Titania Solutions for the Public Sector
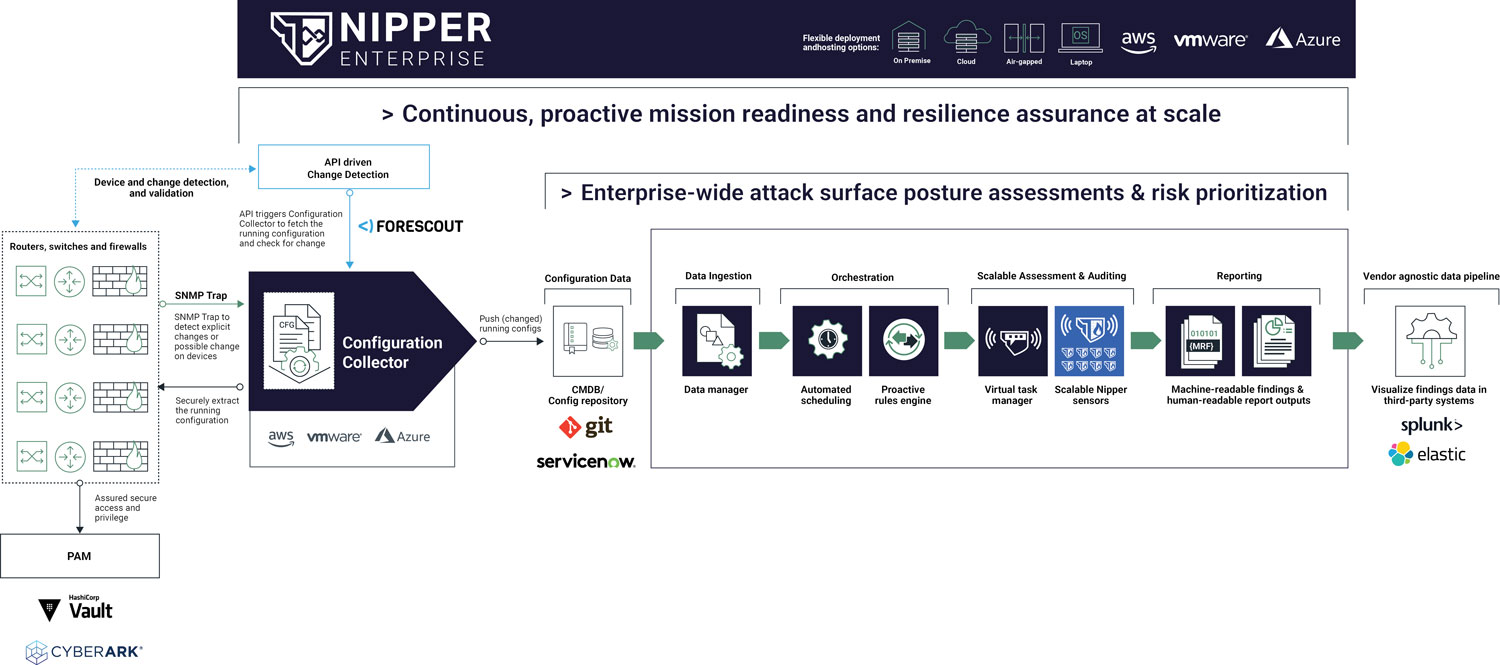
Nipper Enterprise
A comprehensive configuration analysis solution for network infrastructure devices that:
Detects and proactively assesses changed configurations
Detect all network configuration changes, enabling validation of planned versus actual changes and alerting to unauthorized ones, as well as proactive risk assessments of all new/changed configurations.
Provides visibility of attack surface exposure
Analyze segment-by-segment exposure to APTs’ specific tactics, techniques and procedures (TTPs) resulting from network misconfigurations and software vulnerabilities
Alerts to macro segmentation violations
Identify devices with potential critical Zero Trust (ZT) segmentation violations, including unapproved IPs, ports and user accounts
Informs scope of incident response
Reports current and historic attack surface postures to inform scope and focus of response, alerting threat hunters to critical indicators of compromise (IOCs) that are not visible to traffic monitoring solutions.
Ensures operational resilience
Automate configuration monitoring of firewalls, routers and switches that are critical to Important Business System (IBS) segmentation and attack surface management.
Populates and maintains CMDBs
Continuously update a CMDB with live device configurations to expedite disaster recovery as well as to test pre-production changes, ensuring that only secure configurations are deployed into the live environment.
Prioritizes remediation to minimize the attack surface
Focus and expedite remediation and response to assure ongoing operational resilience of business-critical systems and to minimize network attack surface.
Evidences compliance
Automatically reports pass/fail compliance with NIST, STIGs, CIS Benchmarks and PCI DSS to support adherence to mandated compliance requirements.