Explore Tenable's Self-Guided Tours
Tenable and Carahsoft have partnered together to provide a series of self-guided tours of Tenable's products and features. Similar to a live demo, the self-guided tours explores how Tenable's products and features applies to a specific technology vertical such as Cybersecurity.
Learn about Tenable's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Tenable expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
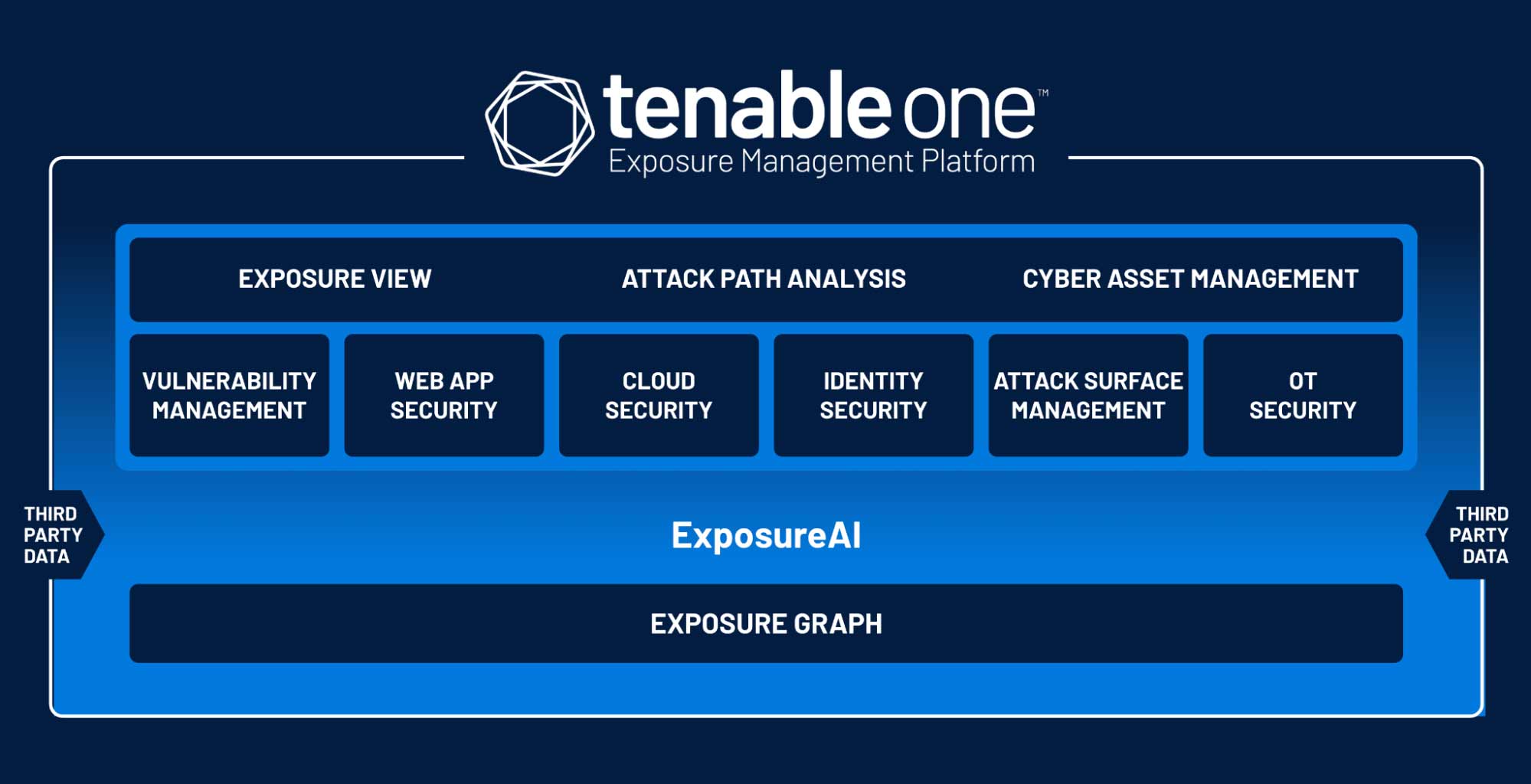
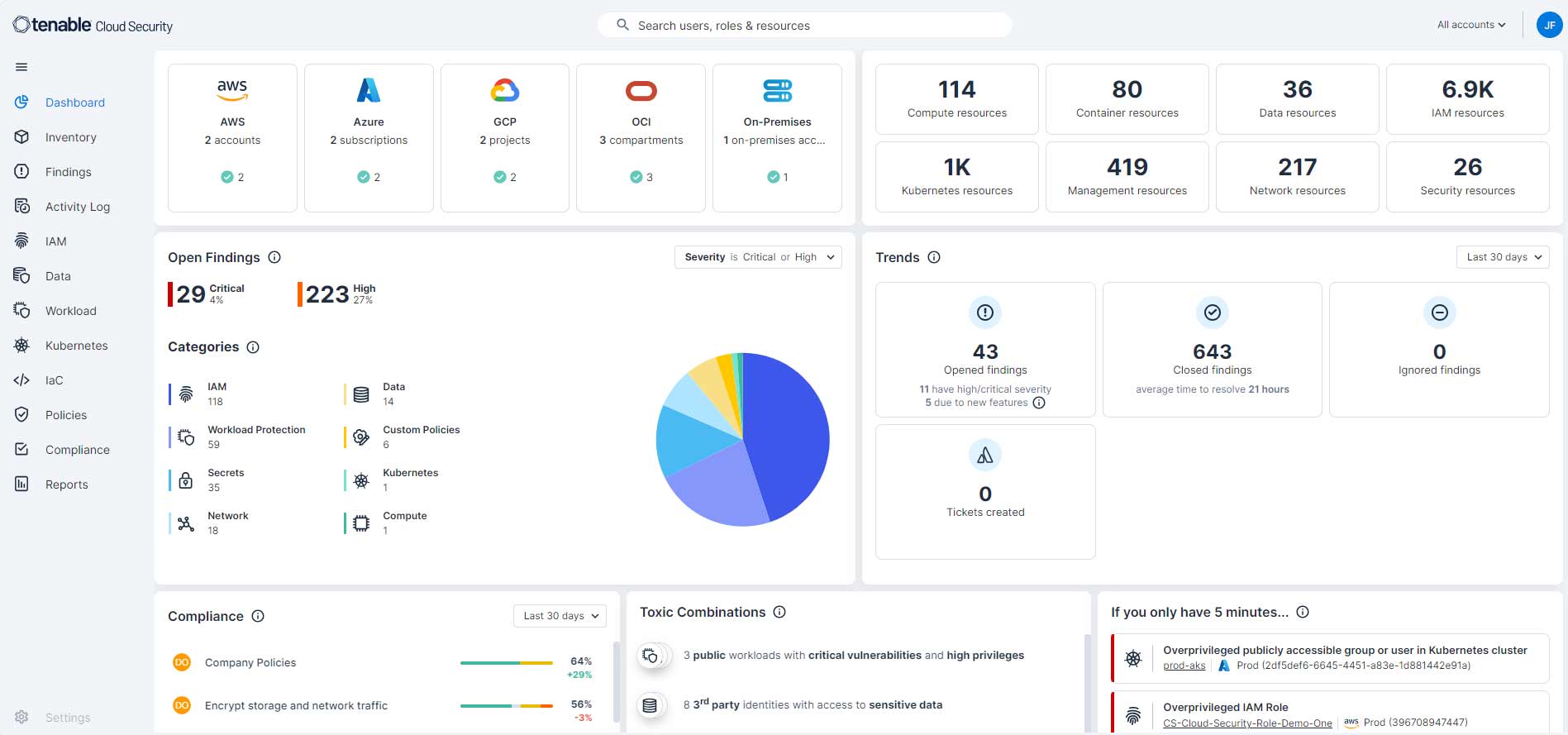
Tenable revolutionizes risk and compliance management with a risk-based approach to vulnerability management, ensuring organizations stay protected in today’s dynamic IT landscape. Traditional vulnerability management tools fall short in addressing the complexities of modern attack surfaces, leaving critical blind spots and failing to provide meaningful context for prioritization.
Tenable’s solution bridges this gap by delivering a unified view of vulnerabilities and their real-world impact, enabling organizations to understand risks in the context of their industry. By prioritizing efforts based on the vulnerabilities that pose the greatest threat, Tenable empowers security teams to maximize efficiency, mitigate risk effectively and safeguard operations against evolving threats.
Want to learn more about Tenable?
Start a self-guided demo now to learn more about automation, risk and compliance.
Tenable’s Benefits Snapshot:
-
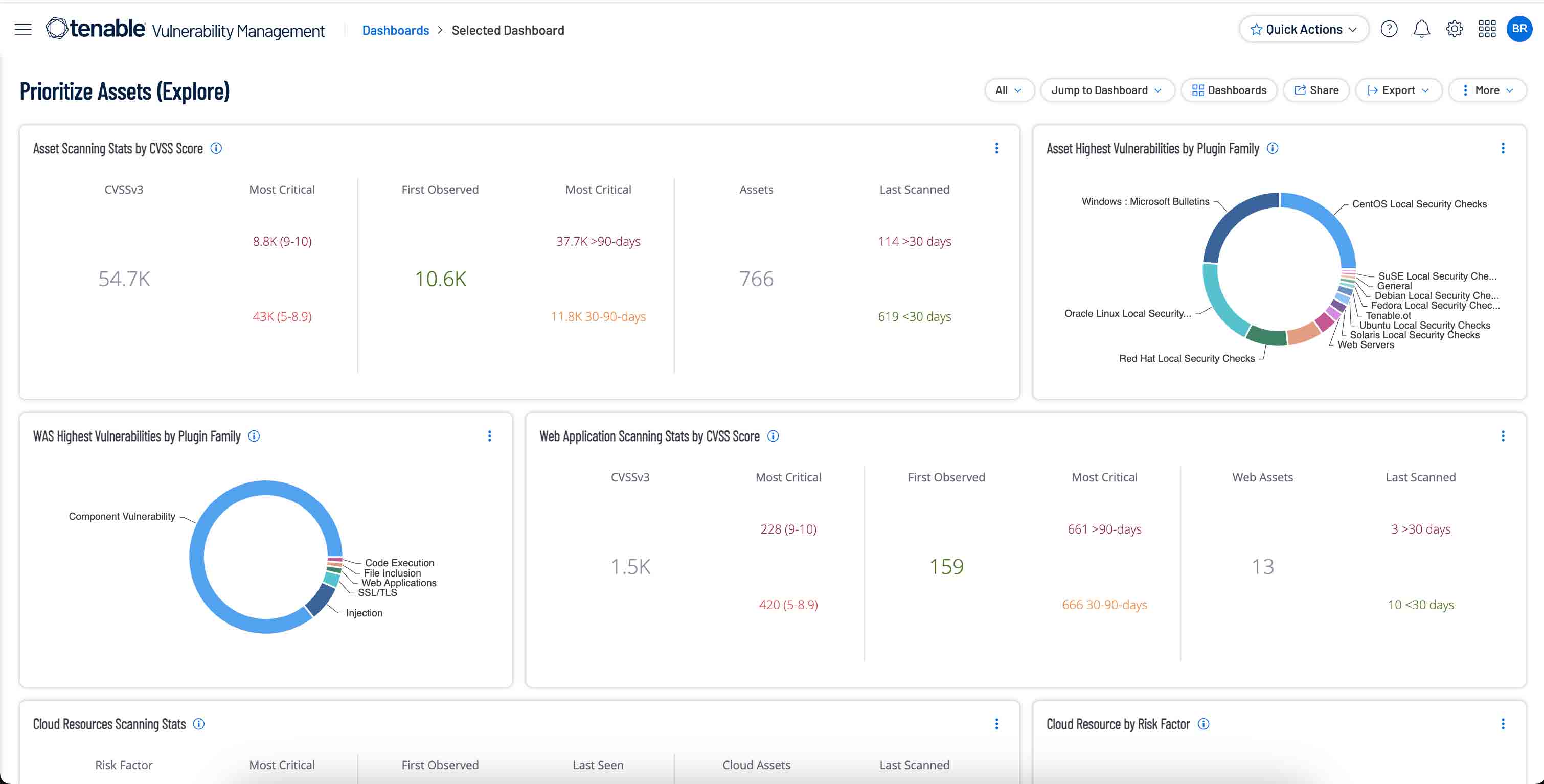
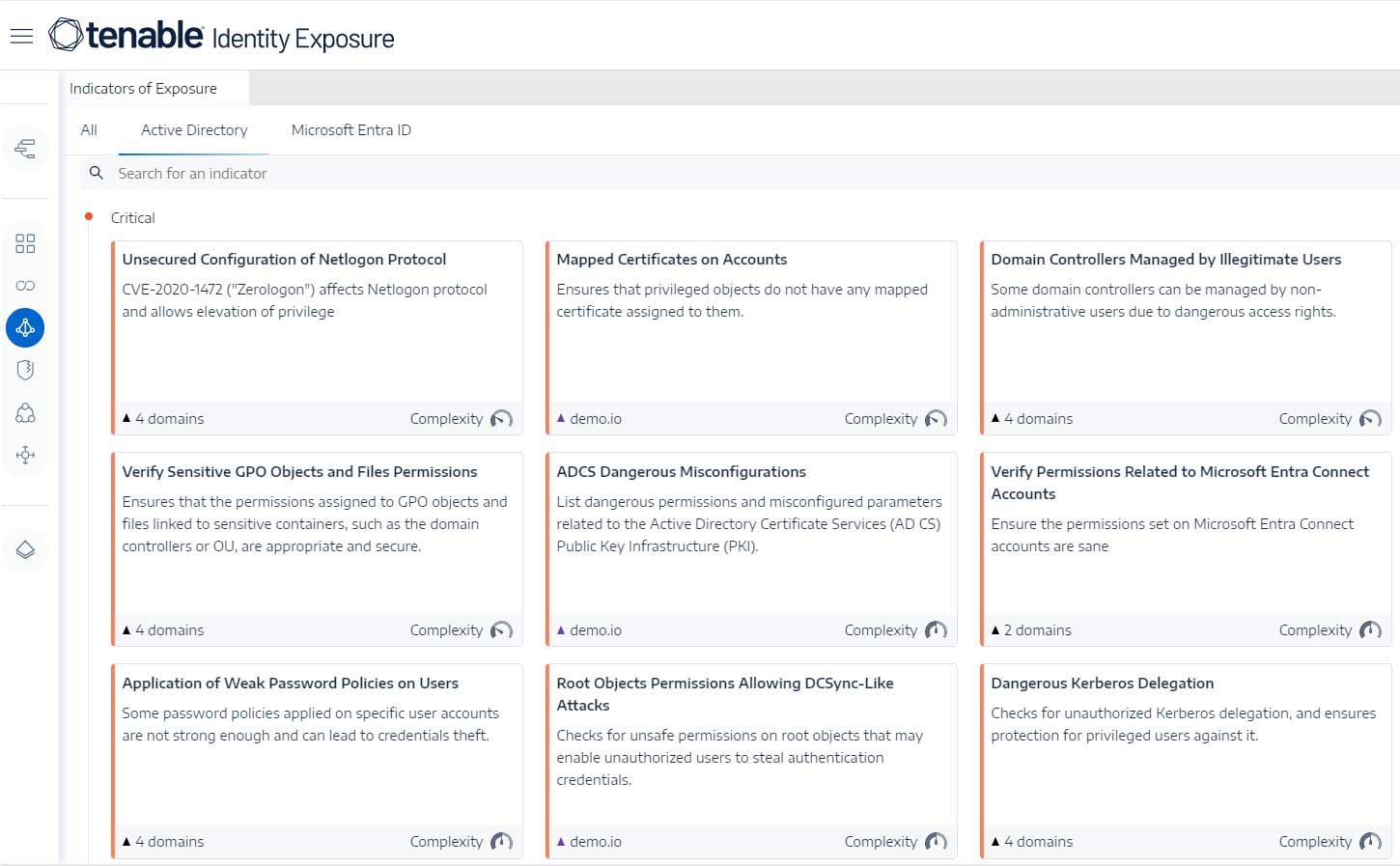
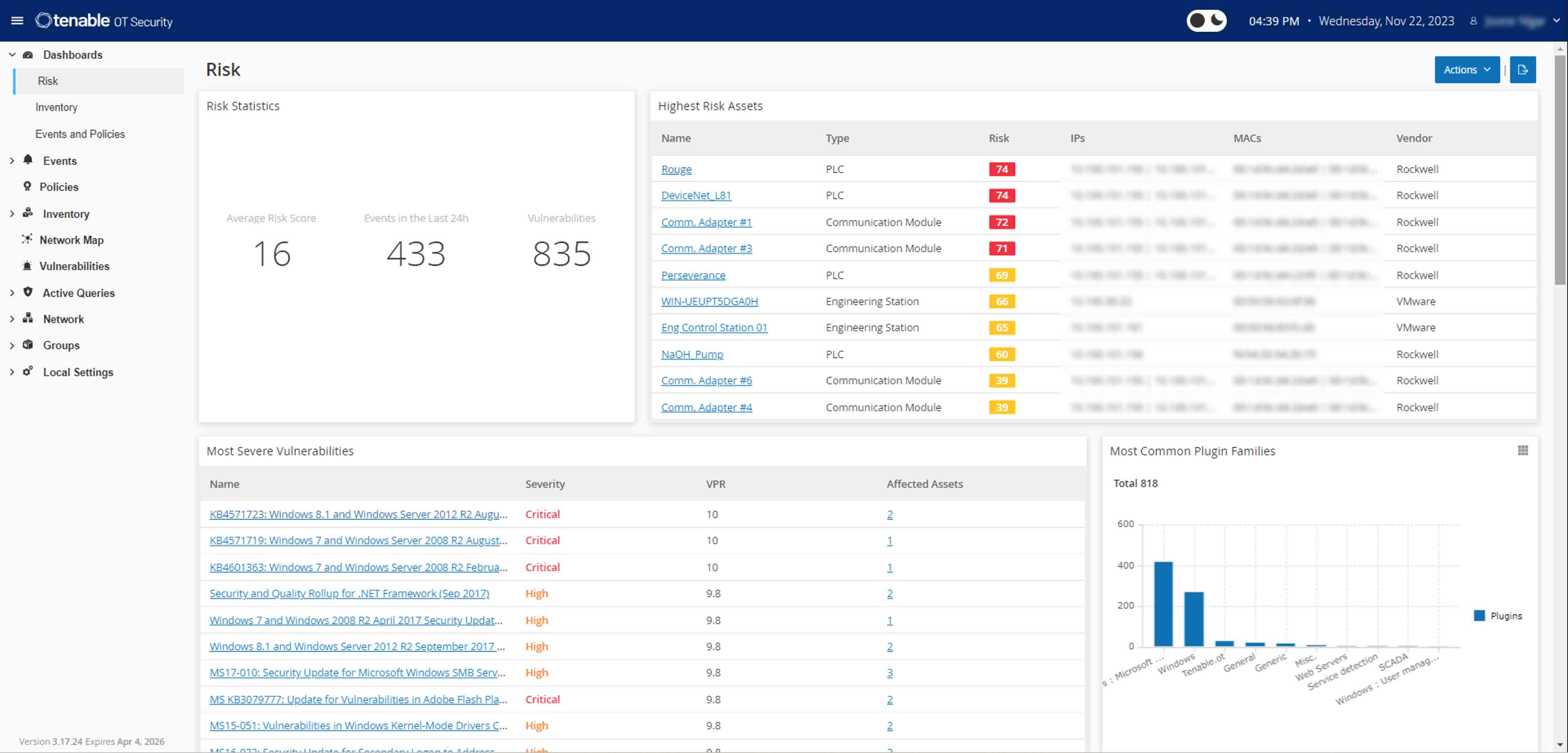
Comprehensive Visibility Across the Attack Surface: Tenable provides comprehensive visibility into an organization's entire attack surface, including IT assets, cloud instances, web applications, Active Directory, and critical infrastructure. This allows public sector organizations to gain a complete understanding of their cyber risk.
-
Risk-Based Prioritization and Remediation: Tenable helps public sector customers prioritize vulnerabilities based on real-world risk and threat intelligence. This enables them to focus efforts on preventing the most likely attacks and rapidly address high-risk vulnerabilities with guided remediation steps.
-
Compliance and Regulatory Adherence: Tenable solutions assist public sector organizations meet stringent compliance requirements including FedRAMP certifications, Executive Orders, CISA BOD mandates and more.