Explore RSA's Self-Guided Tours
RSA and Carahsoft have partnered together to provide a series of self-guided tours of RSA's products and features. Similar to a live demo, the self-guided tours explores how RSA's products and features applies to a specific technology vertical such as Cybersecurity.
Learn about RSA's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a RSA expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
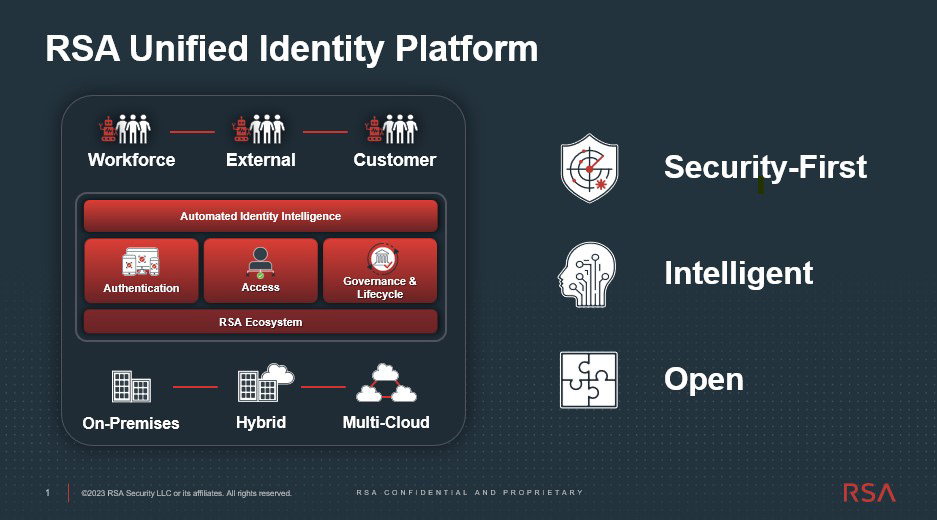
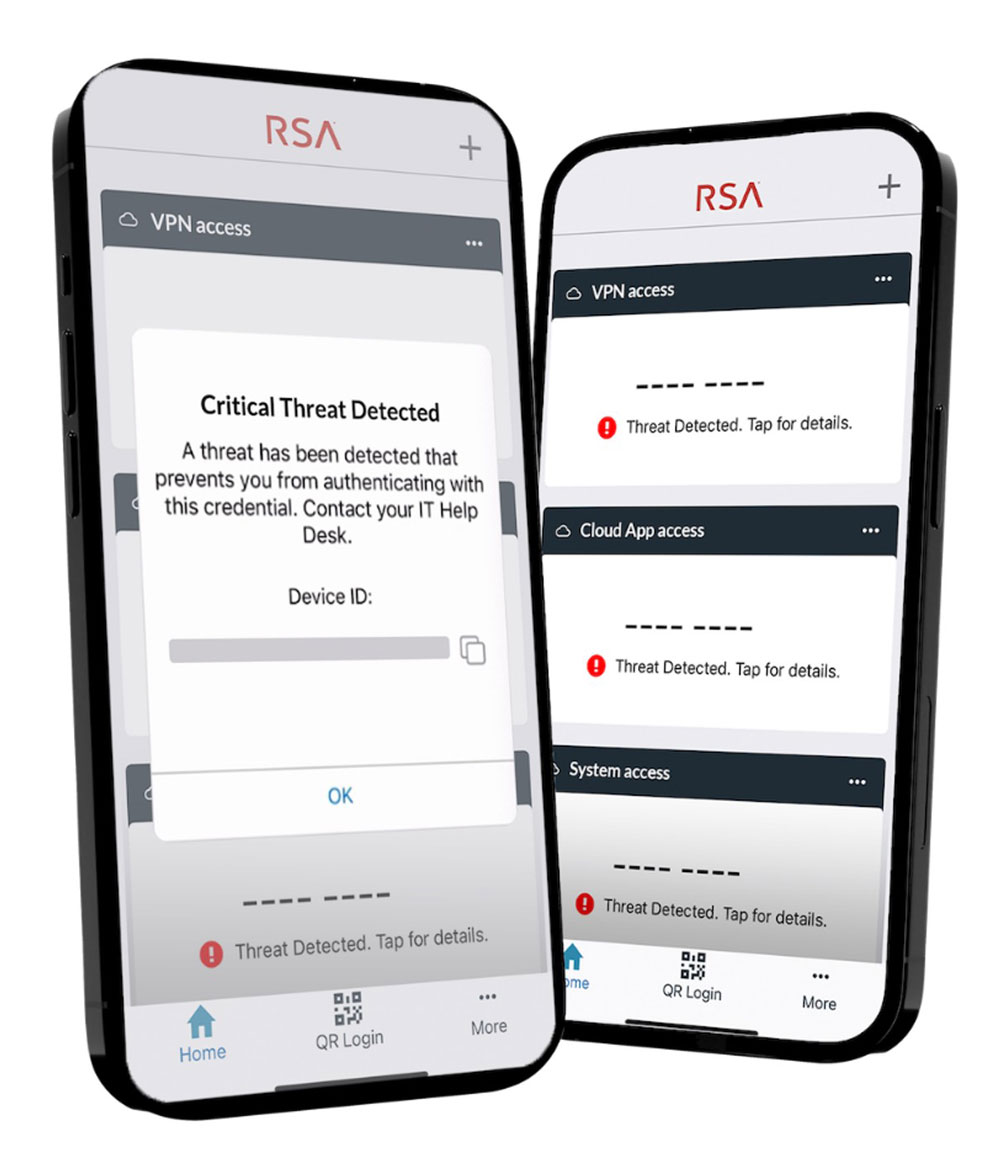
RSA offers an AI-powered Unified Identity Platform designed to safeguard the world’s most secure Government agencies. By integrating access, authentication, governance and lifecycle management into a single solution, RSA addresses cybersecurity vulnerabilities stemming from fragmented identity solutions. Leveraging advanced AI capabilities, the RSA Unified Identity Platform provides agencies with actionable insights to assess risks, automate repetitive tasks and prioritize critical interventions at scale. With a focus on security-first, open and intelligent identity capabilities, RSA empowers agencies to proactively protect against present and future cyber threats, ensuring resilience and security in an ever-evolving digital landscape.
Want to learn more about RSA?
Start a self-guided demo now to learn more about RSA’s cybersecurity solutions.
RSA's Benefits Snapshot:
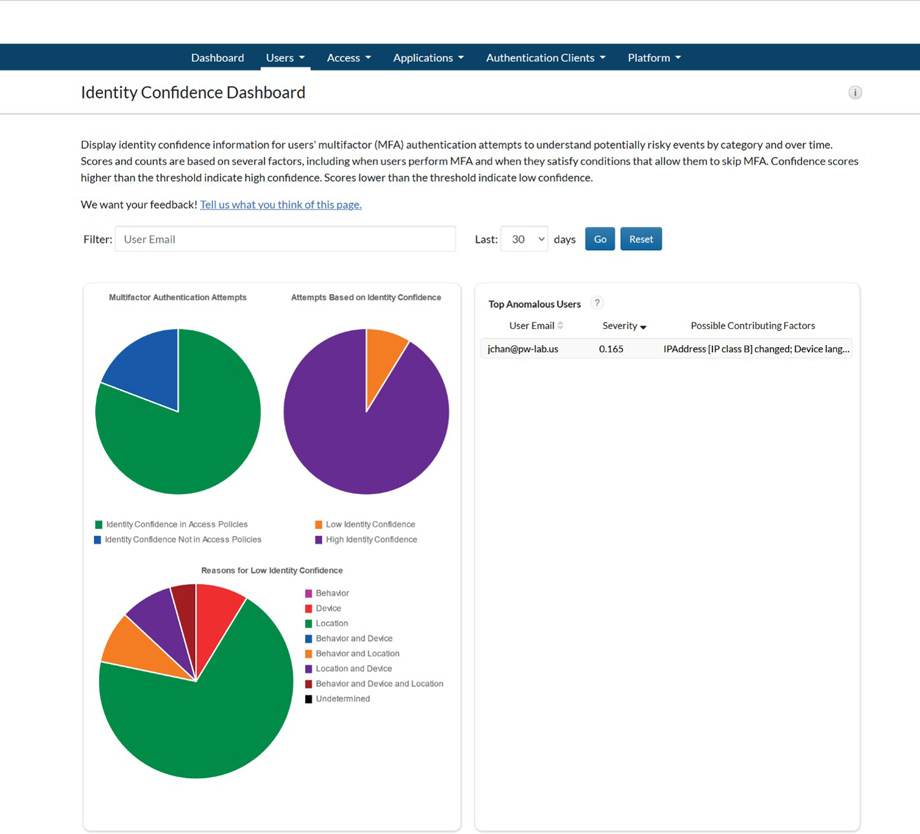
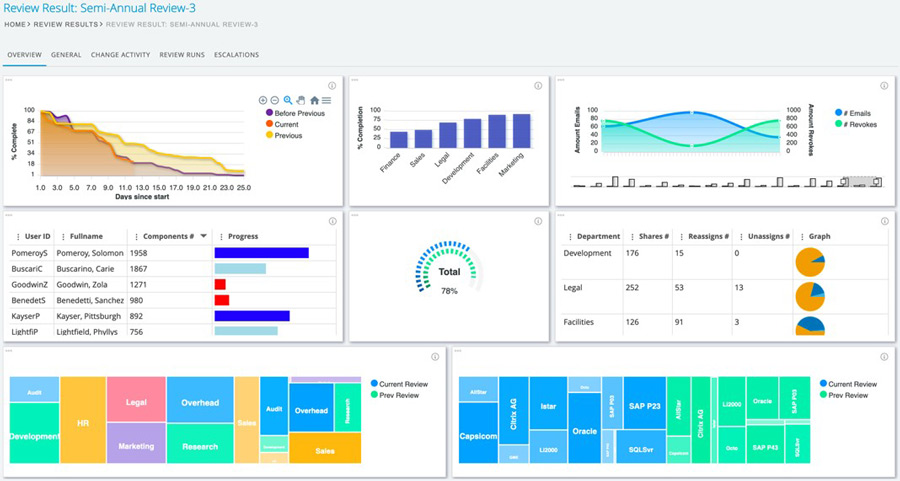
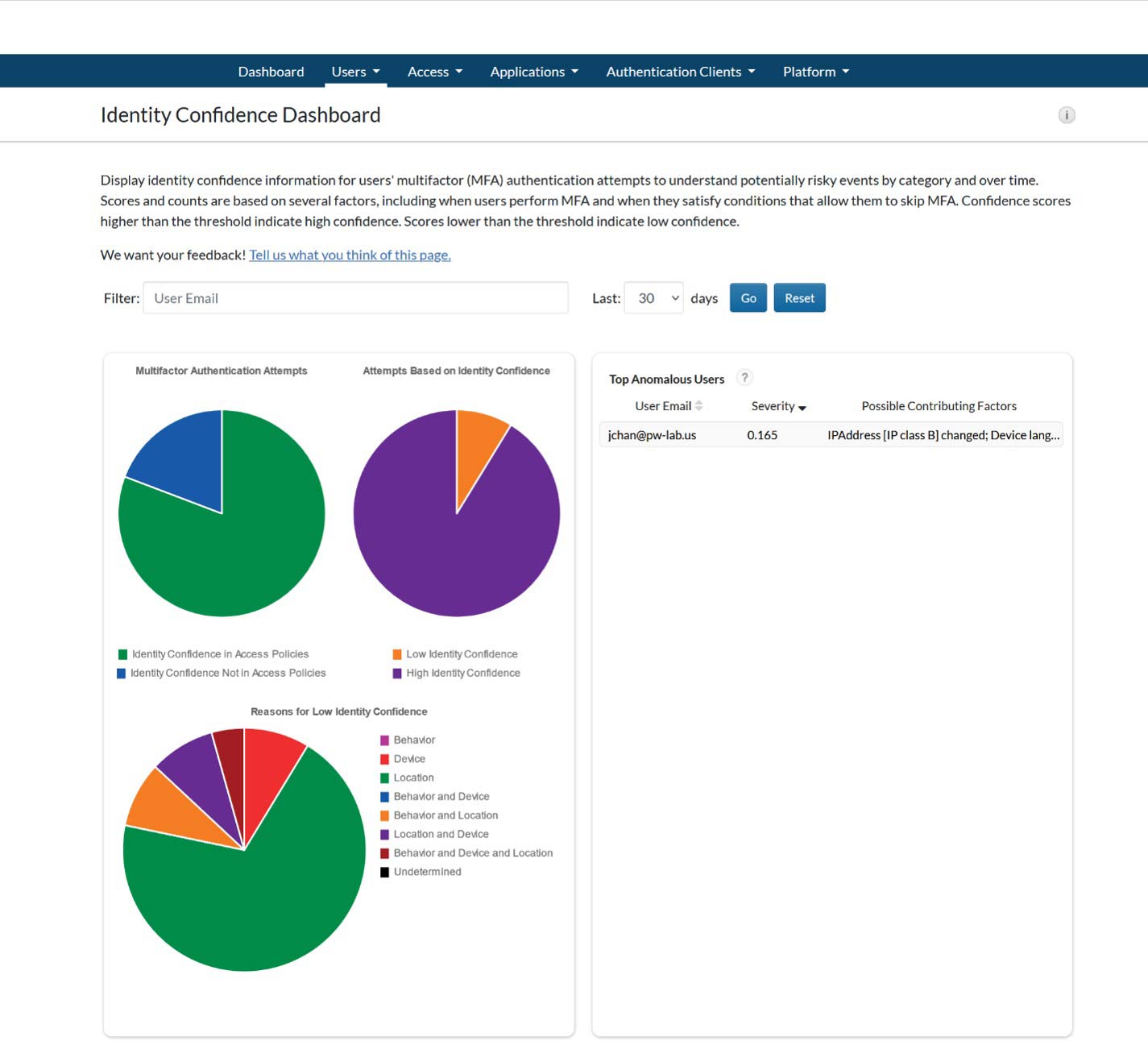
- Minimize human error in entitlement management through automation.
- Enhance operational efficiency through a streamlined credential management process.
- Reduce costs through automation implementation.