Explore Okta's Self-Guided Tours
Okta and Carahsoft have partnered together to provide a series of self-guided tours of Okta's products and features. Similar to a live demo, the self-guided tours explores how Okta's products and features applies to a specific technology vertical such as Cybersecurity and Law Enforcement Technology.
Learn about Okta's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Okta expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
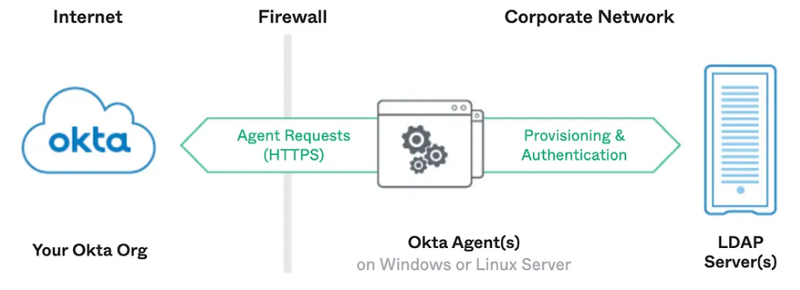
Okta helps Law Enforcement agencies and Police Departments meet Criminal Justice Information Services (CJIS) requirements by providing strong access control, advanced authentication and logging. Agencies can streamline IT operations through the secure management of apps and multi-cloud environments in a single identity platform.
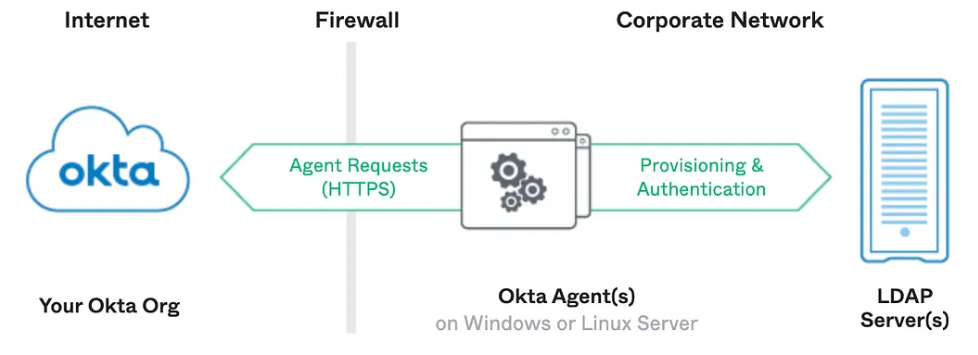
Okta is the world’s leading identity solution with a powerful and extensible platform that is easy-to-use and integrates with existing solutions. Okta complies with multiple regulatory standards, including SOC2, ISO 27001 and 27018 and has a FedRAMP Moderate Authority to Operate (ATO).
Want to learn more about Okta?
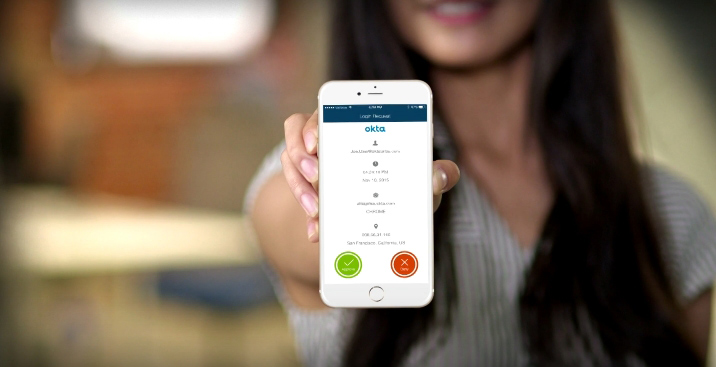
Start a self-guided demo now to learn how to use Okta with CJIS.
Okta’s Benefits Snapshot:
- Automate processes with little to no-code options
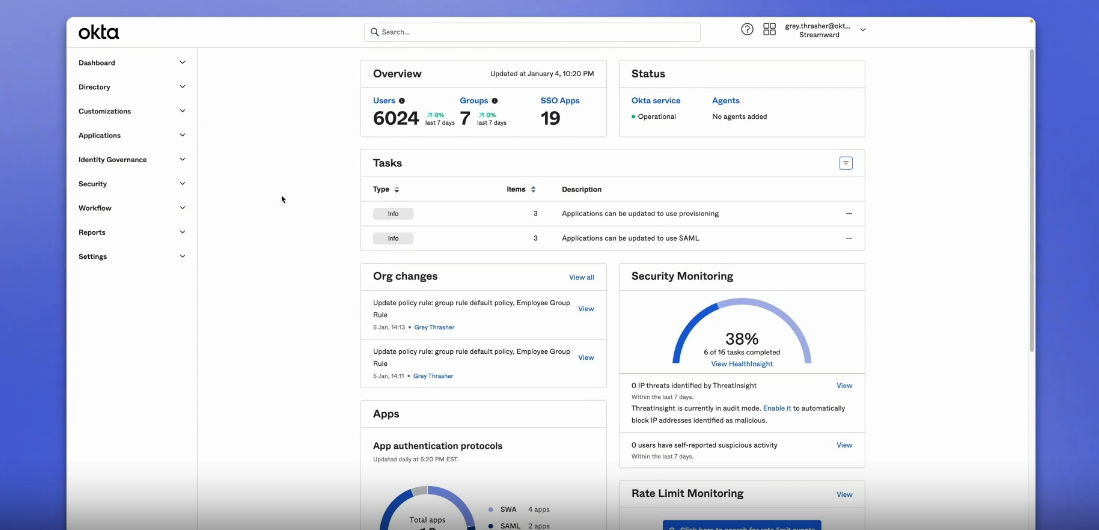
- Get a central admin console to manage all users, apps and policies
- Accelerate operations with Zero Trust solutions
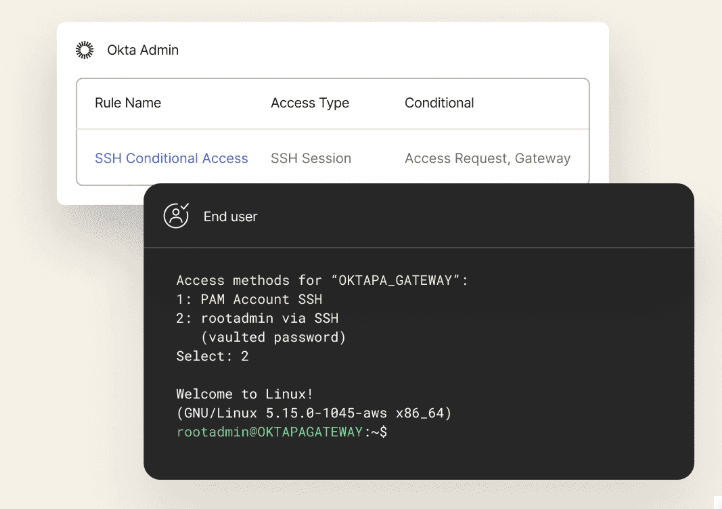
In today’s ever-evolving threat landscape, traditional security perimeters are no longer sufficient to safeguard Government assets. To address this challenge, Okta offers robust support for Zero Trust architecture, empowering agencies to fortify their security posture against sophisticated threats. With Zero Trust being a collaborative endeavor, Okta emphasizes the importance of unified efforts through its Integration Network, providing pre-built, deep integrations that enable technologies to work seamlessly together. By seamlessly integrating identity solutions across diverse technology ecosystems and partnering with industry-leading security providers, Okta enables agencies to adopt a holistic approach to Zero Trust.
Want to learn more about Okta?
Start a self-guided demo now to learn more about Okta’s comprehensive cybersecurity solutions.
Okta's Benefits Snapshot:
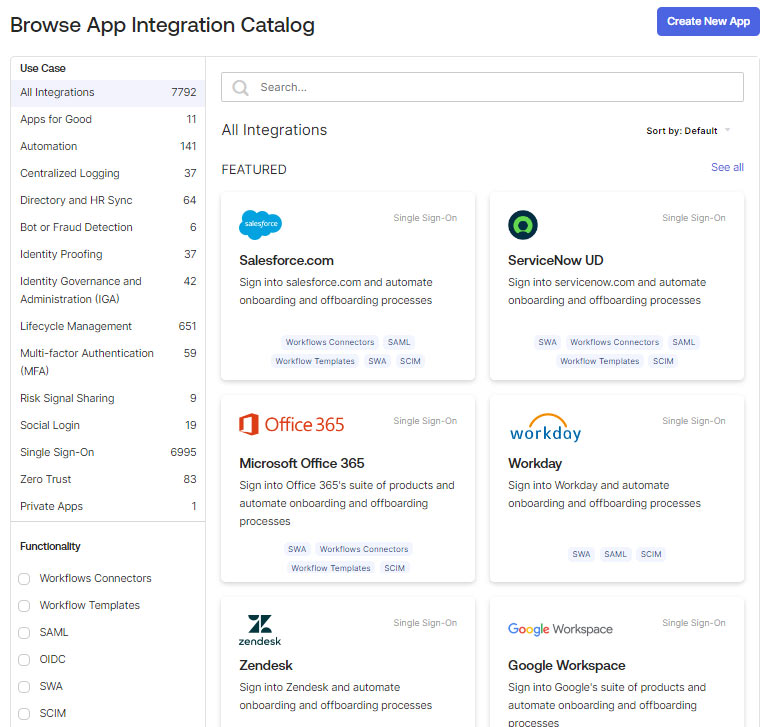
- Applications: Single Sign-On (SSO) into 7,000+ and provision users to over 250 cloud and on-prem apps.
- Infrastructure as a service: Connect IT and developers to public cloud computing services securely.
- Zero Trust Strategy: Integrate your identity solution across your entire technology ecosystem seamlessly.