Explore GuardStack's Self-Guided Tours
GuardStack and Carahsoft have partnered together to provide a series of self-guided tours of GuardStack's products and features. Similar to a live demo, the self-guided tours explores how GuardStack's products and features applies to a specific technology vertical such as 5G.
Learn about GuardStack's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a GuardStack expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
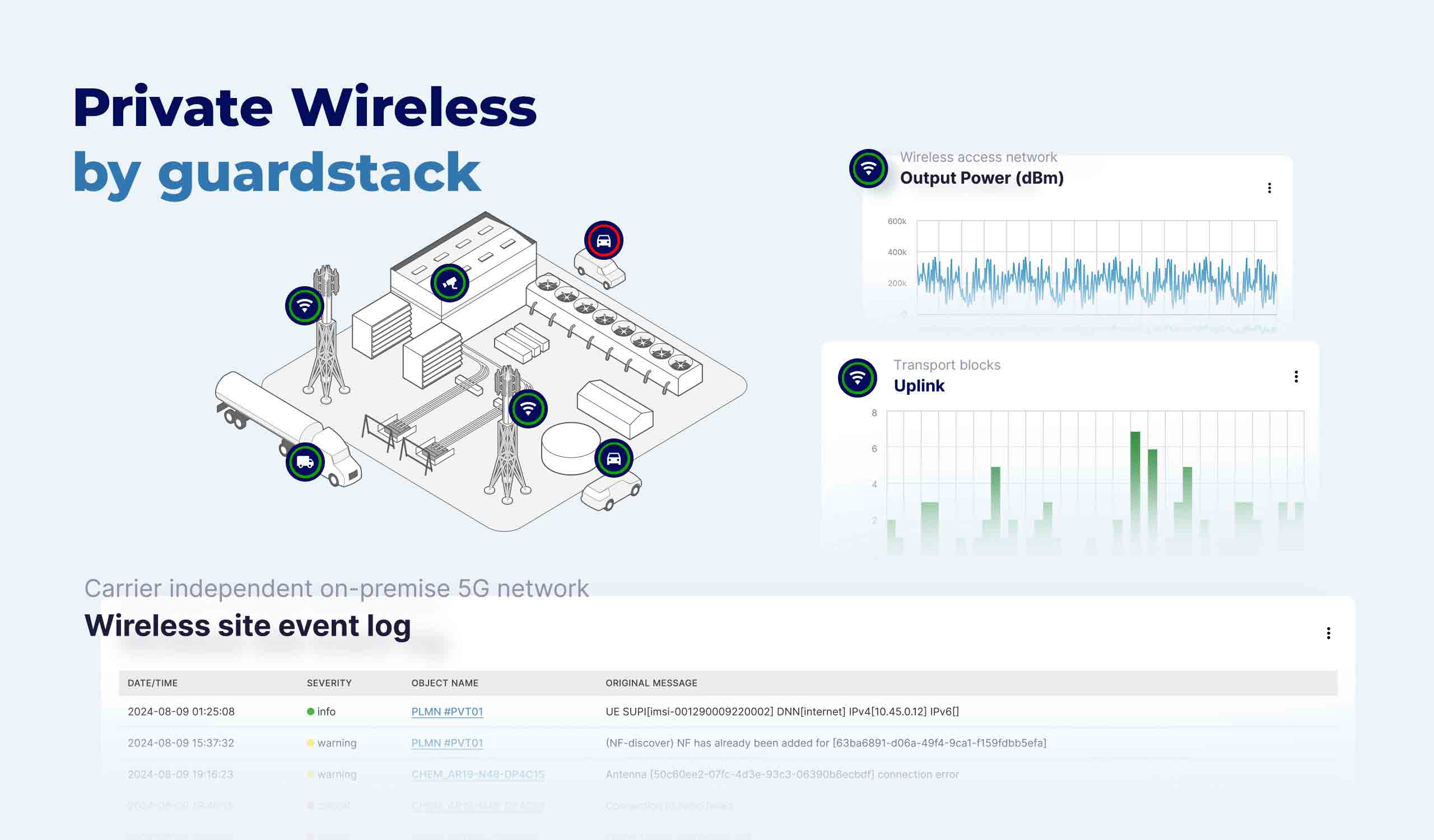
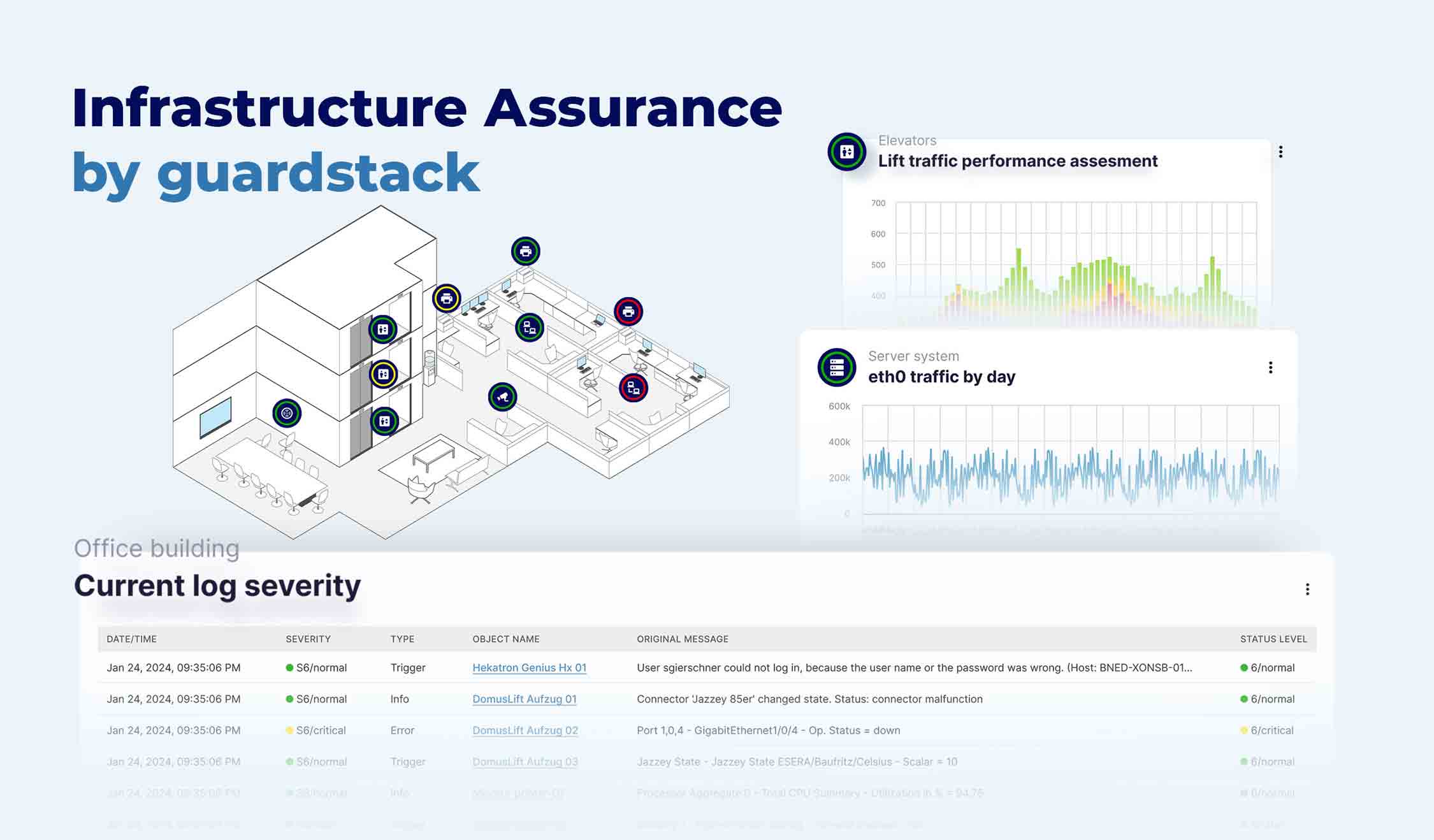
GuardStack provides a flexible and simplified 5G solution for enterprises to deploy and control their private campus networks, ensuring independence from public network operators. By managing wireless network infrastructure, GuardStack empowers agencies with full control over their networks and users. The holistic software solution orchestrates communication and data collection across various system boundaries, seamlessly connecting diverse transmission media from established radio systems to cutting-edge 5G technology. With predictive intelligence, cybersecurity integration and an intuitive user interface, GuardStack enables efficient data utilization, ensuring sustainable and long-term competitiveness.
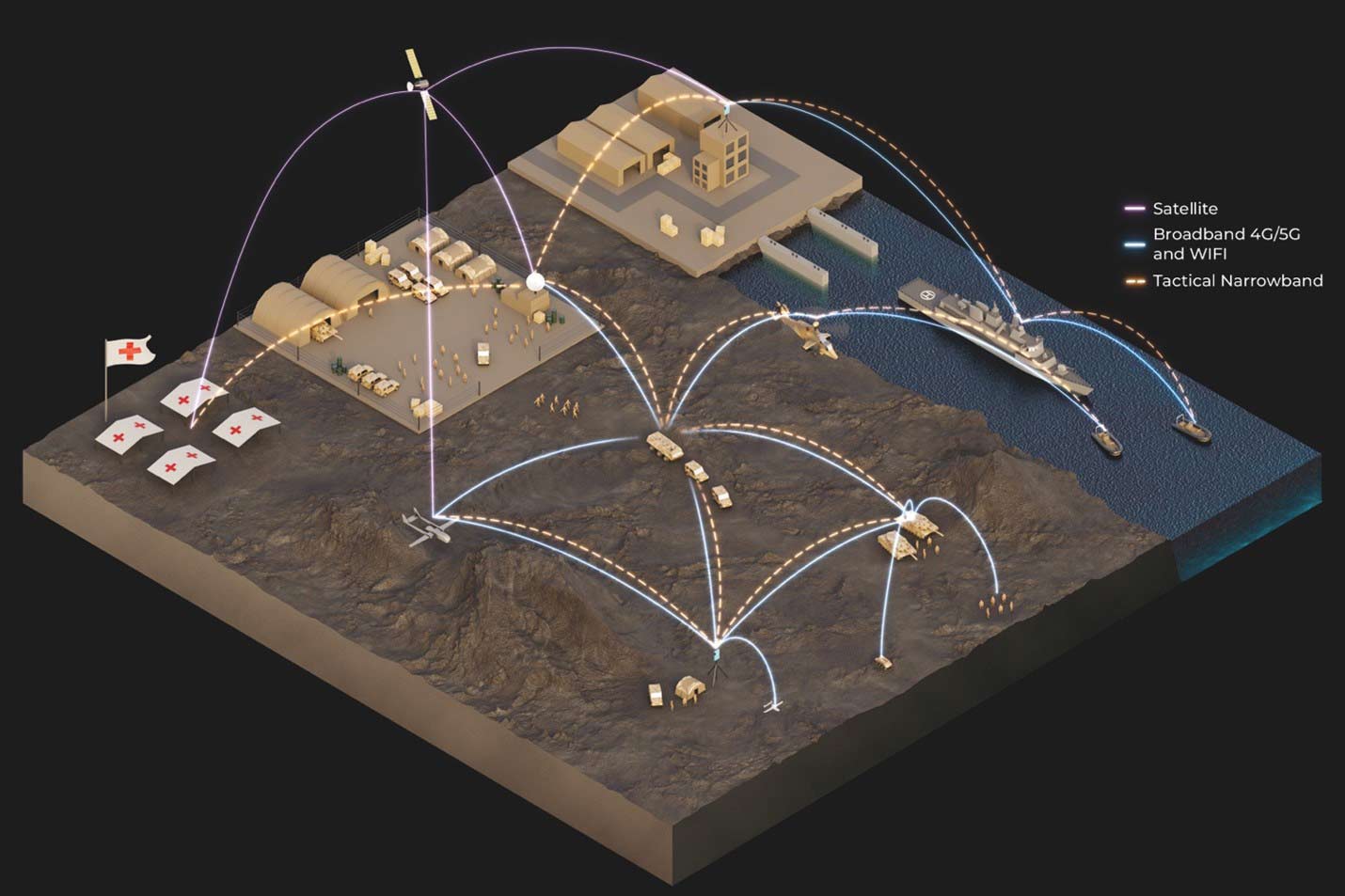
Additionally, GuardStack enhances situational awareness for armed forces in various operations through its advanced broadband communication networks, including 4G and 5G. The platform bridges the gap between commercial communication infrastructures and military networks, meeting stringent operational requirements for effective communication at the tactical edge. Supporting the Digitalization of Land-Based Operations (D-LBO) program, GuardStack provides and information and communication network that connects the lowest tactical level with the core network of the Bundeswehr IT system, enhancing operational efficiency and decision-making in dynamic environments.
Want to learn more about GuardStack?
Start a self-guided demo now to learn more about advanced communications technologies and data collection.
GuardStack’s Benefits Snapshot:
- Capture any data for seamless visibility in the cloud or on-premises with GuardStack’s investigative approach.
- Resolve issues faster with intelligent solution recommendations based on processing rules to quickly identify serious incidents.
- Encrypt data end-to-end to meet stringent security standards.