Explore Gigamon's Self-Guided Tours
Gigamon and Carahsoft have partnered together to provide a series of self-guided tours of Gigamon's products and features. Similar to a live demo, the self-guided tours explores how Gigamon's products and features applies to a specific technology vertical such as Cybersecurity.
Learn about Gigamon's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Gigamon expert from Carahsoft. Start a Self-Guided Tour now by selecting one below:
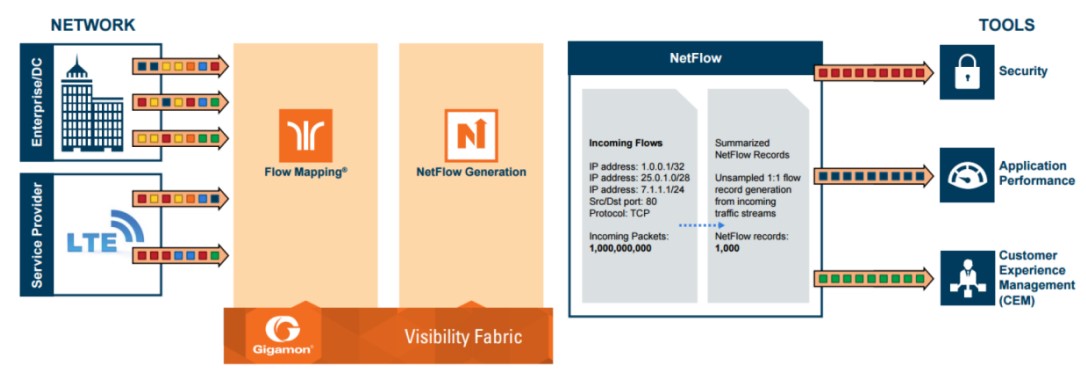
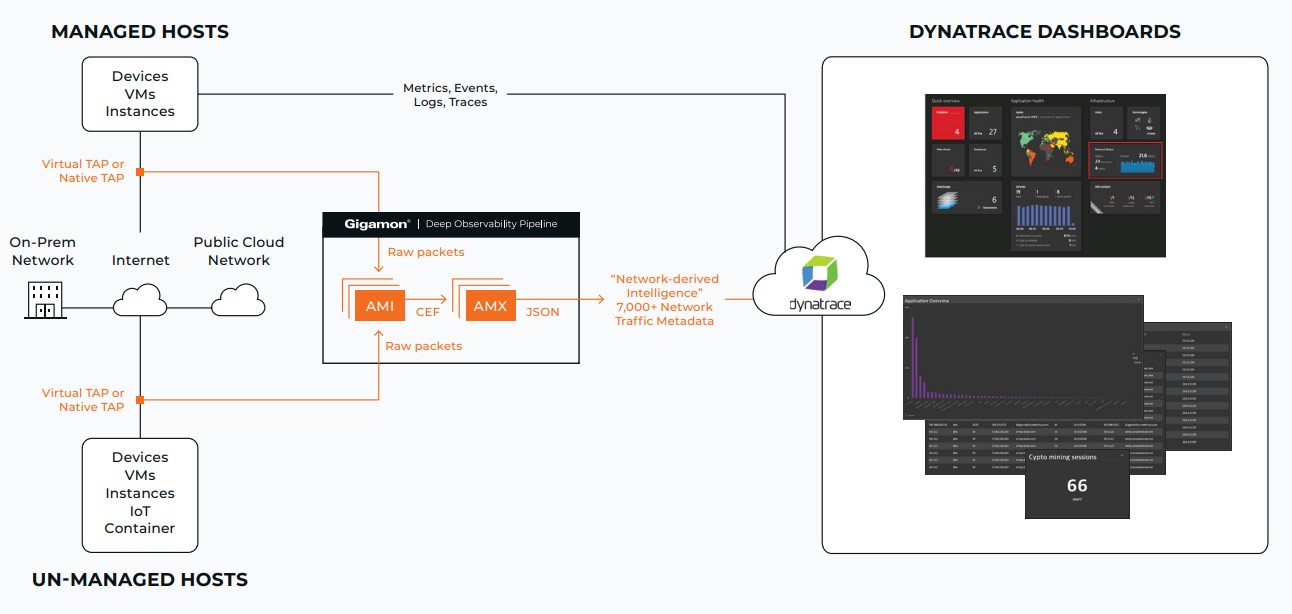
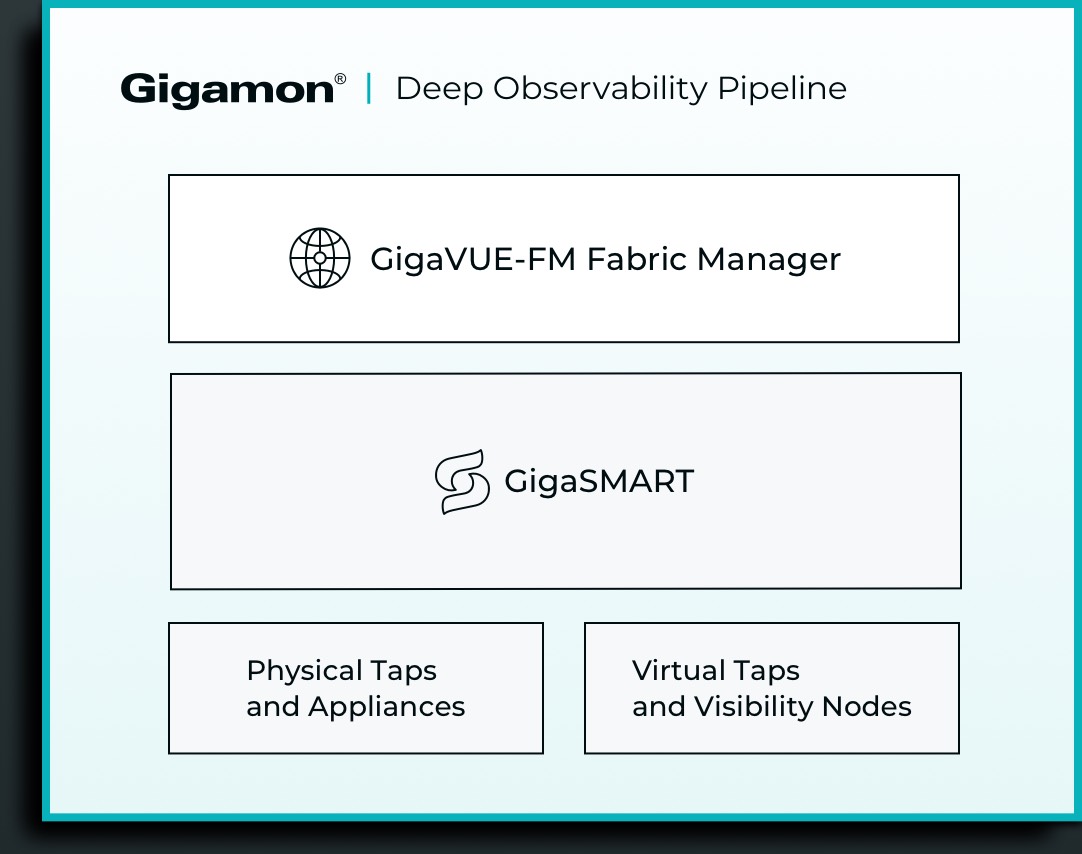
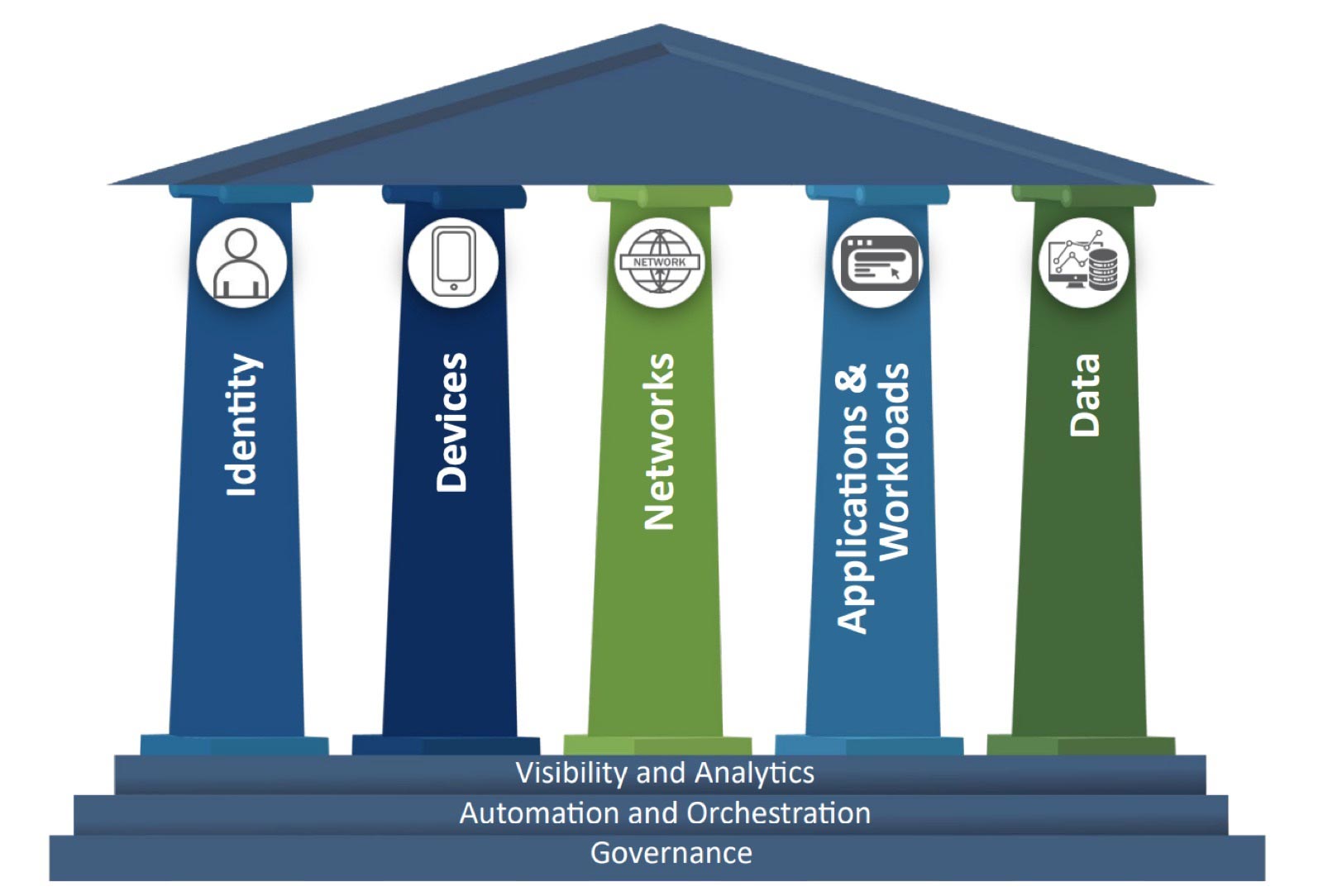
Gigamon leads the forefront of cybersecurity innovation by offering a robust observability pipeline that leverages actionable network-derived intelligence to enhance the effectiveness of an agency’s cloud, security and observability tools. This integrated approach ensures not only security and compliance governance but also accelerates root-cause analysis of performance bottlenecks, while simultaneously reducing operational overhead associated with managing hybrid and MultiCloud IT infrastructures. By transcending conventional security and observability methodologies reliant solely on metrics, events, logs and traces (MELT) data, Gigamon delivers unparalleled value. Real-time network intelligence derived from packets, flows and application metadata enables a defense-in-depth strategy and comprehensive performance management across diverse cloud environments. Through proactive threat identification and rapid anomaly detection, Gigamon empowers agencies to fortify their security posture, mitigate risks and expedite troubleshooting, thus elevating cybersecurity to new heights of effectiveness and efficiency.
Want to learn more about Gigamon?
Start a self-guided demo now to learn more about Gigamon’s cybersecurity solutions.
Gigamon’s Benefits Snapshot:
- Embrace a proactive security and compliance approach to reduce risk exposure.
- Establish a robust digital infrastructure to enhance productivity, agility and organizational resilience.
- Channel IT resources towards accelerating cloud initiatives to drive top-line growth effectively.