Explore Elastic's Self-Guided Tours
Elastic and Carahsoft have partnered to provide a series of self-guided tours for Elastic's enterprise-ready DevSecOps, Geospatial and Cybersecurity solutions. Similar to a live demonstration, these in-depth walkthroughs explore Elastic's wide array of use cases that can help meet you and your organization’s unique IT needs.
Learn about Elastic’s DevSecOps, Geospatial and Cybersecurity solutions by starting a self-guided tour below or schedule time with your dedicated Elastic representative for personalized insights.
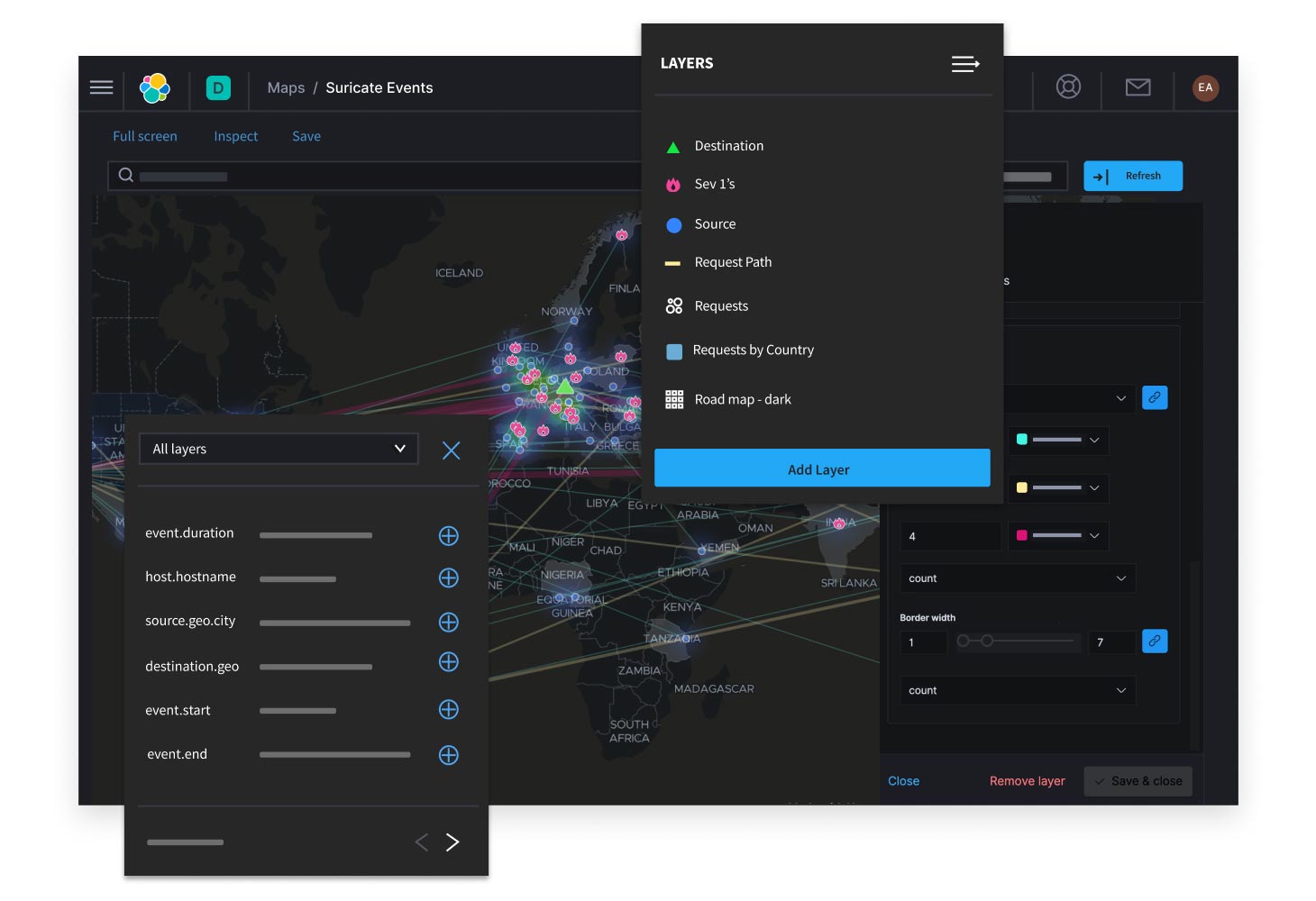
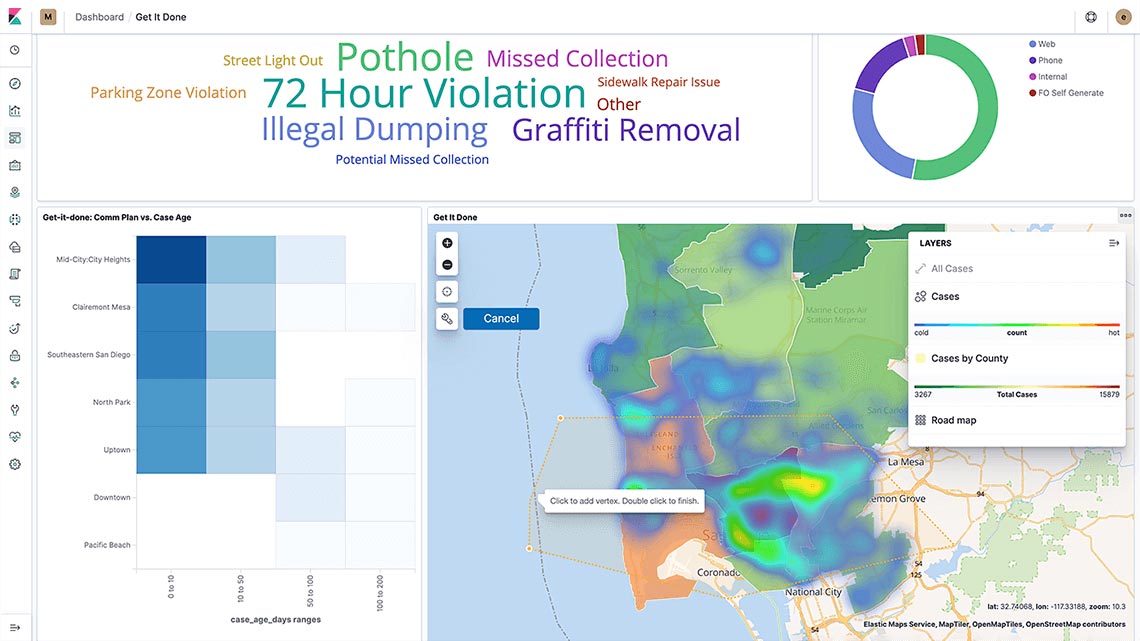
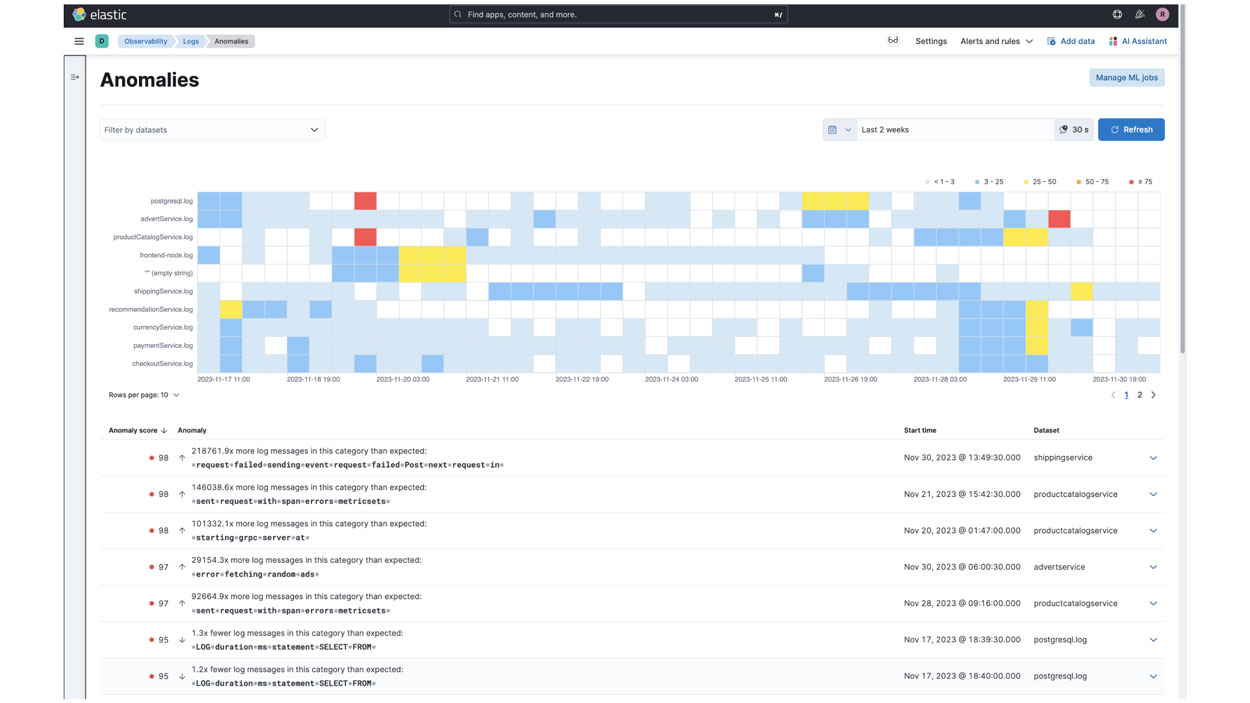
Elasticsearch enables rapid storage and querying of geospatial data. Kibana, their platform for geospatial analysis and action, detects anomalies, sends notifications and solves location-based challenges. Use the Maps app within Kibana’s dashboard to analyze geospatial data, identify patterns, explore points of interest and set up location-based alerts. Utilize the Elastic Stack's geospatial capabilities to explore, analyze, and discover spatial insights in data. Elasticsearch’s search and aggregation power, combined with Kibana’s visualizations in the Maps app, enable efficient handling of location-driven questions and proximity queries. Start with one geo use case and easily expand with the automatic scalability of the Elastic Stack.
Want to learn more about Elasticsearch?
Start a self-guided demo now to learn more about Elasticsearch’s geospatial capabilities.
Elastic Search's Benefits Snapshot:
- Advanced ML and analytics accelerate problem resolution with open, flexible and unified observability.
- A unified solution at scale automates protection, investigation and response with SIEM, EDR and cloud security.
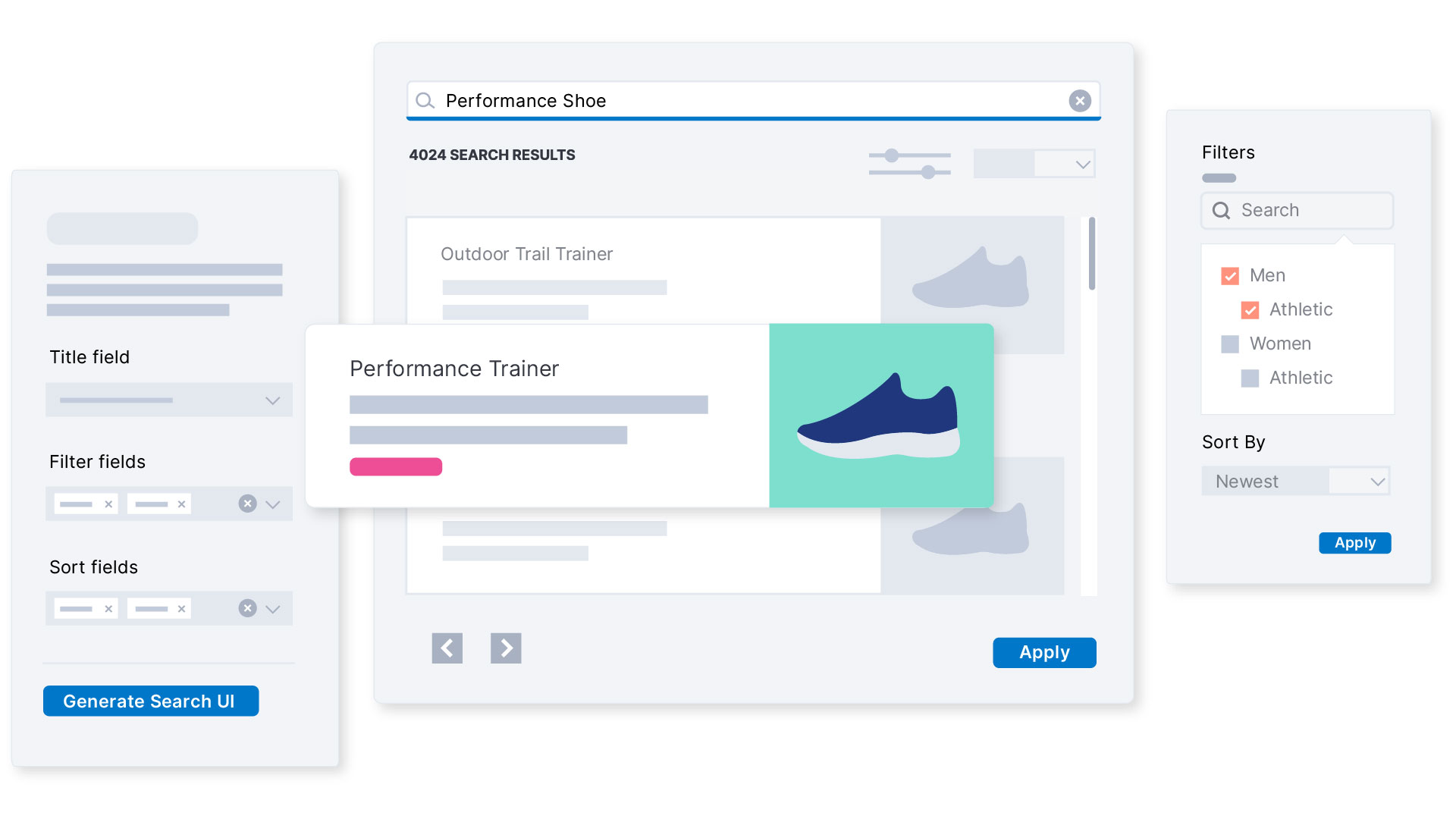
- Build powerful AI/ML enabled search applications for users and employees.
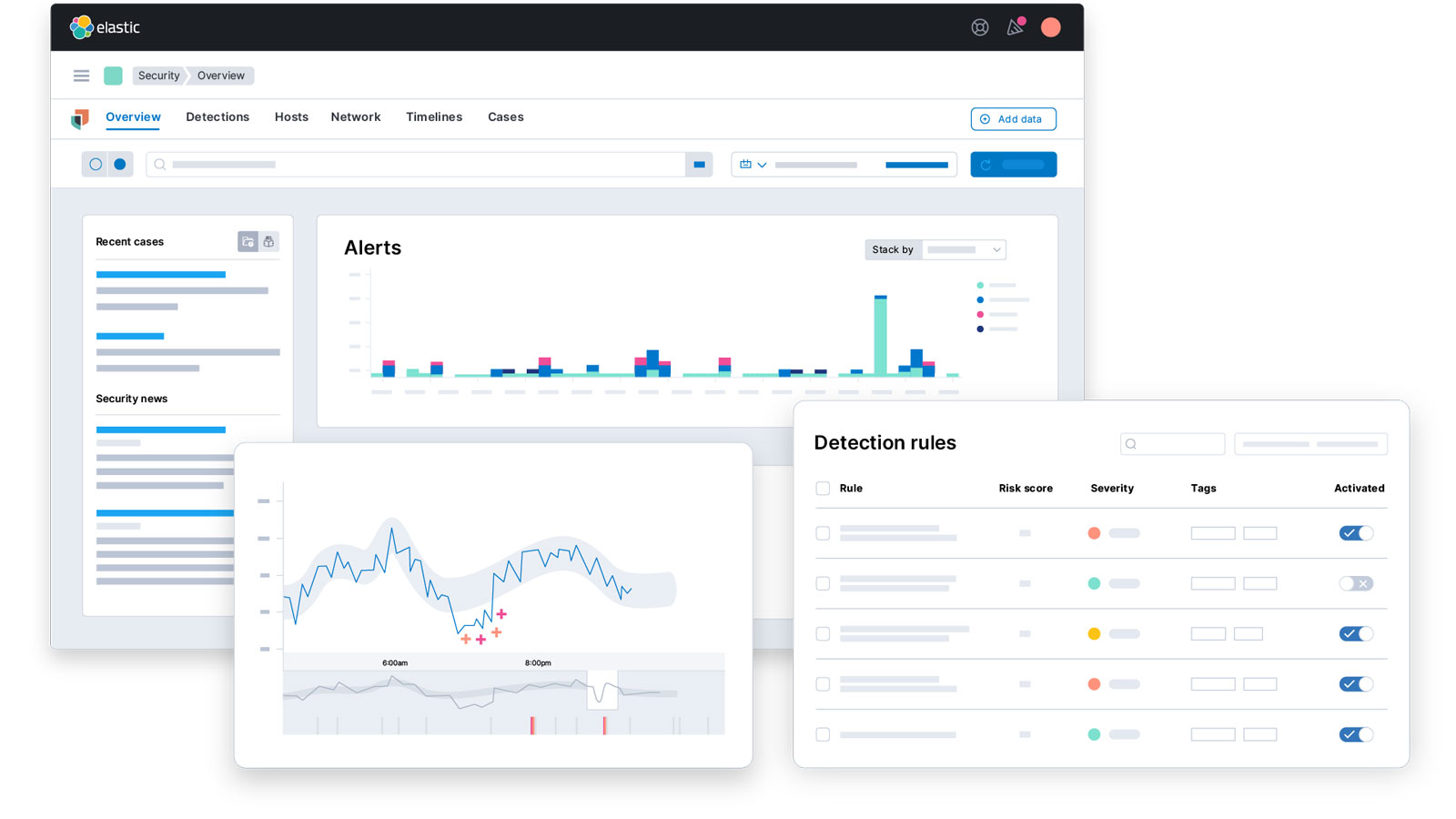
Elastic intertwines open source principles with cybersecurity innovation, streamlining the process for developers to integrate robust search functionality into their applications while bolstering security measures. By furnishing cybersecurity personnel with cutting-edge Security Incident and Event Management (SIEM) tools, Elastic fortifies agencies’ detection and response capabilities, serving as a vital connective data layer within Zero Trust strategies. Within the realm of National Security, Elastic’s scalable search platform empowers users to elevate intelligence analysis by harnessing secure data, thus enhancing situational awareness and enabling confident safeguarding of the nation’s security interests. Renowned for its expertise in sensitive data ingestion, enrichment and secure sharing, Elastic amplifies the potency of crucial data at the speed and scale essential for mission accomplishment in agency settings.
Want to learn more about Elastic?
Start a self-guided demo now to learn more about Elastic’s data collection, search power and threat detection.
Elastic’s Benefits Snapshot:
- Build enterprise search into your agency’s databases, websites and apps.
- Achieve NSM-8 Compliance with Elastic’s unified data foundation.
- Prevent, detect and respond to threats through automation and data analysis.
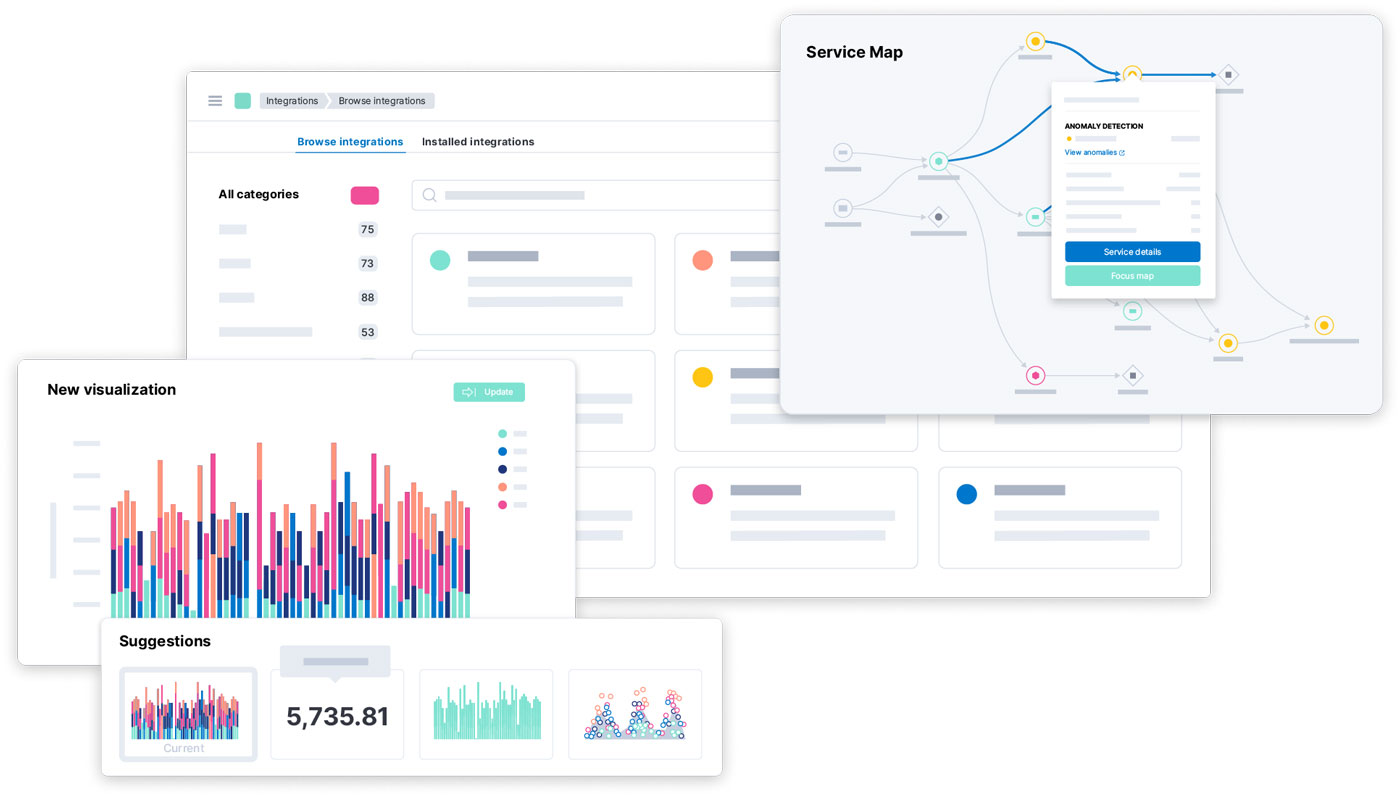
The Elastic Stack, an open source search-based technology, is extremely fast, enabling the intake, analysis and secure access of data. Capture and analyze every layer of development by integrating Elastic into existing DevSecOps infrastructure and data sources, adding power and flexibility to operations. Elastic unifies data to help monitor and troubleshoot systems, enabling development teams to work together more efficiently making and deploying reliable and secure software. Developers gain complete observability of application performance and security across the DevSecOps infrastructure, they can monitor, measure and analyze every step of their CI/CD pipelines.
Want to learn more about Elastic?
Start a self-guided demo now to learn how to protect, investigate and respond to complex threats.
Elastic's Benefits Snapshot:
- Elasticsearch provides fast searching across data sources, the key to making critical business decisions, identifying performance issues and detecting threats.
- Monitor, measure and analyze CI/CD pipelines from a performance and availability standpoint, as well as for business KPIs.
- Support enterprise search, observability and security operations with Elastic Stack’s pre-configured, auto-scaling artifacts.