DoD Impact Level
The Department of Defense Cloud Computing Security Requirements Guide (CC SRG) establishes a standardized guideline for Cloud Service Providers (CSPs) that serve the Defense community. Built upon the FedRAMP baseline, the CC SRG adds additional layers of security and risk management protocols necessary to protect sensitive DoD information within various cloud environments.
Carahsoft supports a wide portfolio of CSPs that meet CC SRG requirements, ensuring DoD components have access to secure, compliant cloud solutions. As a trusted procurement vehicle, we enable Defense agencies to efficiently acquire the cloud technologies they need to meet CC SRG requirements and achieve their mission objectives.
Why is DoD Compliance Important?
Protecting DoD data is a top priority due to highly sensitive, classified nature of Defense agency’s information. The CC SRG was created to ensure that any cloud environment used by the DoD is secure, resilient and capable of defending against evolving cyber threats. By adhering to stringent guidelines outlined in the CC SRG, CSPs demonstrate their ability to safeguard DoD data across various impact levels, from unclassified to classified environments.
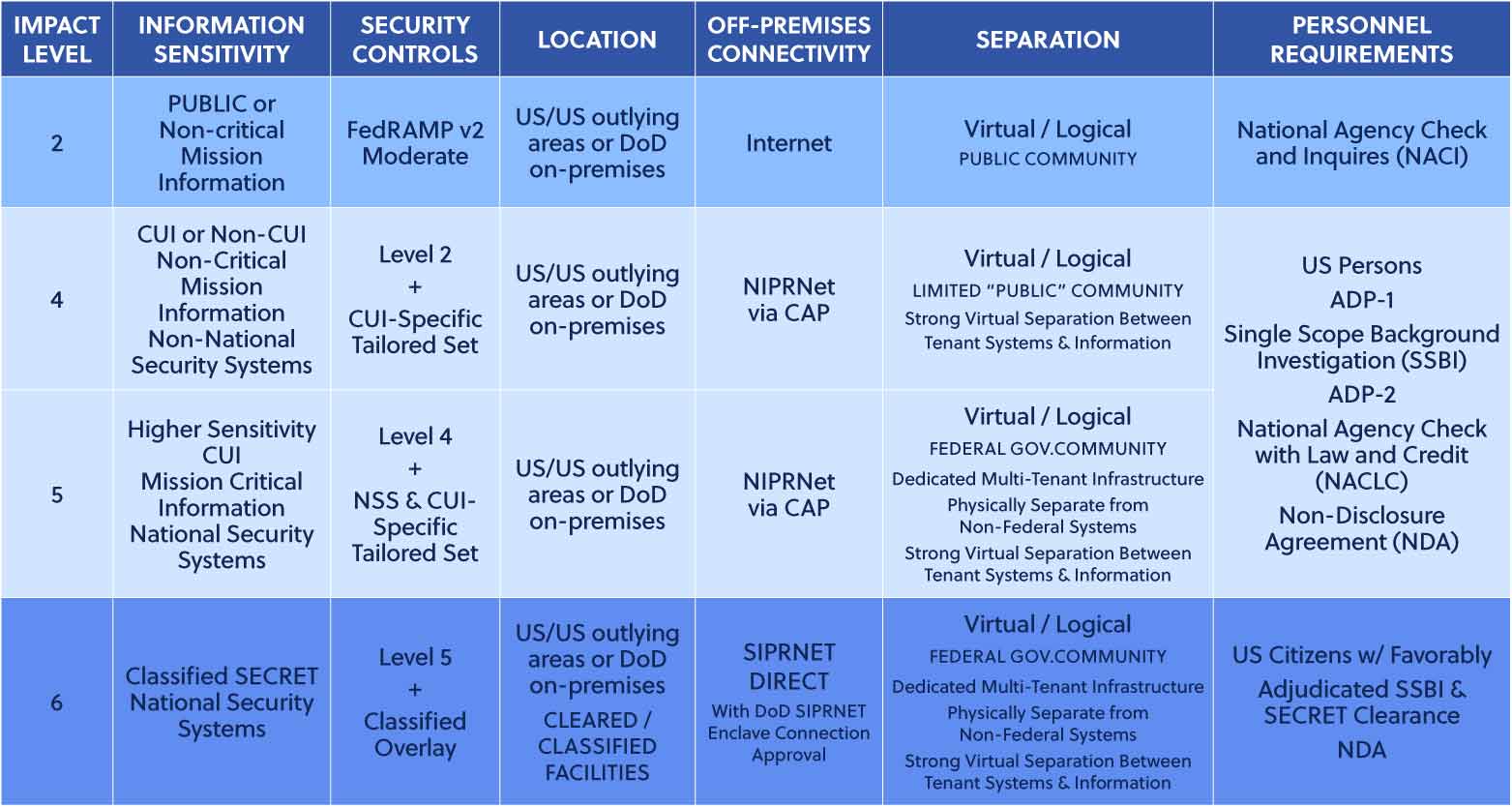
DoD Impact Levels (IL) Explained
The DoD CC SRG categorizes cloud environments by distinct impact levels based on the sensitivity of the data they handle and the potential consequences of a security breach. The chart below provides an overview of each impact level, from handling publicly available data to securing the most sensitive classified information.
Carahsoft’s DoD IL Help Desk
The Carahsoft DoD IL help desk provides Defense agencies with procurement support for CSOs aligned with DISA guidelines while also helping our technology partners navigate the security requirements for cloud providers working with the DoD. Contact a DoD IL expert through our help desk to learn more.

FedRAMP Reciprocity with DoD Cybersecurity Requirements
The DoD recognizes reciprocity between certain FedRAMP and DoD CC SRG authorization levels. FedRAMP Moderate aligns with Impact Level 2 (IL2), the lowest level of authorization under the CC SRG. IL2 is applicable to CSOs that store, process or transmit publicly available or non-critical mission data. The baseline security requirements for IL2 are equivalent to those of FedRAMP Moderate.
In 2019, the Defense Information Systems Agency (DISA) enabled DoD IL2 data to be hosted on CSOs authorized at the FedRAMP Moderate level without requiring additional written authorization from the DoD. This has streamlined the procurement process for DoD agencies by enabling them to leverage FedRAMP authorized solutions for IL2 workloads. However the CSO must meet certain conditions including being listed as “authorized” on the FedRAMP marketplace, having data centers located within the U.S. or its territories and maintaining authorization status though continuous monitoring.
DoD IL Resources
Whitepaper


|
DOD IL RESOURCE
Ping Identity has expanded its FedRAMP High and DoD IL5 offerings with key identity and access management (ICAM) capabilities, helping federal agencies enhance security, compliance, and user experience. These new features, including multi-factor authentication, identity governance, and lifecycle management, streamline identity processes while ensuring high-level protection for government entities and suppliers.
|
> |
 |
DOD IL RESOURCE
UberEther ATO Advantage Offering datasheet for DoD IL 4 & 5
|
> |