AVAILABLE 24x7
888.662.2724
AVAILABLE 24x7
(888) 66CARAH
Fast & Accurate
Request A Quote
Quick Response
Chat With Us
Carahsoft, in conjunction with its vendor partners, sponsors hundreds of events each year, ranging from webcasts and tradeshows to executive roundtables and technology forums.
Government Events and Resources
Events
Resources
Featured
To learn more about improving the user experience, GovLoop spoke with Docusign, a major supplier of digitization solutions to government. This report explains how digitizing and automating processes can improve productivity, user satisfaction and security.Learn how digitizing and automating processe...

360 Logistics ensures safe traveling within your own organization. Knowmadics 360 Logistics unveils the pioneering all-in-one solution for integrated logistics and travel risk management.
FileCloud offers a solution for content collaboration for public sector organizations seeking to meet stringent data residency and security requirements. Our flexible platform allows you to choose where your data is stored, ensuring compliance with Zero Trust and other government regulations and min...
Dell Technologies and H2O.ai engineering teams collaborate to design tested and tuned systems optimized for your AI and ML workloads. View this datasheet to learn how Dell Technologies and H2O.ai team up to improve customer experiences, streamline processes, and decrease waste and fraud.

The first intelligent automation platform for hybrid and multi-cloud big compute
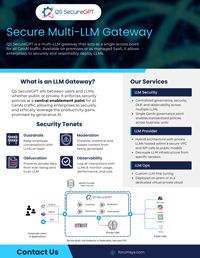
Discover how QS SecureGPT can help your agency securely manage all Generative AI traffic through a single, centralized multi-LLM gateway. This powerful tool enforces security policies, providing centralized governance and observability for both private and public LLMs. Download the datasheet now to ...
Discover AI with Prepared. This comprehensive toolkit offers an overview of AI, explores how 911 centers can optimize AI to mitigate staffing shortages and cope with increasing call volumes, and discusses its role in streamlining data. Gain deeper knowledge with two detailed use cases.
Unlock the secrets to measurable sustainability gains in our new e-book. Explore actionable tips like optimizing energy usage and promoting diversity for environmental, economic, and social benefits. Discover why integrating sustainability into your management solution is essential. Dive in now to e...
This serves as a comprehensive guide to understanding the role of APIs in modern digital business strategies. The playbook outlines key API management practices, covering the API lifecycle, security, integration, and how businesses can leverage APIs to create scalable and secure digital ecosystems.
This eBook describes how Silverfort can help educational environments protect and prevent themselves against ransomware attacks. Outlining how their implementation of Silverfort MFA (Multi-Factor Authentication) Protection in educational institutes can help eliminate surging ransomware attacks on st...