AVAILABLE 24x7
888.662.2724
AVAILABLE 24x7
(888) 66CARAH
Fast & Accurate
Request A Quote
Quick Response
Chat With Us
Carahsoft, in conjunction with its vendor partners, sponsors hundreds of events each year, ranging from webcasts and tradeshows to executive roundtables and technology forums.
Government Events and Resources
Events
Archived Events

Multi-Vendor Training
Event Date: June 15, 2022
Hosted By: Red Hat, F5 & Carahsoft
Location: Lincoln, MA
Hosted By: Red Hat, F5 & Carahsoft
Location: Lincoln, MA
As the U.S. Air Force looks to streamline and accelerate operations, modernization has become a key initiative for mission critical success. An app-centric approach to application delivery helps to enable intelligent scaling at the point of a bottleneck, eliminating the need to scale infrastructure across the entire ...

Red Hat Webcast
Event Date: May 26, 2022
Hosted By: Red Hat & Carahsoft
Hosted By: Red Hat & Carahsoft
Evolving technical demands and resource constraints are spurring public sector teams to embrace innovative solutions that support IT modernization, at scale.Red Hat OpenShift, an enterprise-ready Kubernetes container platform built for an open hybrid cloud strategy, provides your ...

Red Hat Webcast
Event Date: May 17, 2022
Hosted By: Red Hat, TVAR & Carahsoft
Hosted By: Red Hat, TVAR & Carahsoft
Zero Trust is built around the idea of moving away from a single network perimeter to a layered defense with carefully controlled gateways. This model assumes everything is running independently and is always exposed to potential ...

Multi-Vendor Webcast
Event Date: May 05, 2022
Hosted By: Nutanix, Red Hat, HPE & Carahsoft
Hosted By: Nutanix, Red Hat, HPE & Carahsoft
On May 5th, attendees of this webinar discovered how Red Hat OpenShift on Nutanix and HPE simplifies application modernization efforts. This certified solution of Red Hat Openshift is the industry-leading enterprise Kubernetes platform built for hybrid cloud, powered by the Nutanix Cloud Platform- the market-leading ...

Multi-Vendor Webcast
Event Date: May 04, 2022
Hosted By: F5, Red Hat, WWT & Carahsoft
Hosted By: F5, Red Hat, WWT & Carahsoft
Red Hat's Ansible Automation platform is the leading enterprise-ready automation platform helping network operators save time and reduce risk. Traditional approaches to network configuration can slow applications and make them prone to errors. Simple, powerful, agentless and proven, Ansible Automation Platform brings network ...

Multi-Vendor Training
Event Date: April 22, 2022
Hosted By: Red Hat, Splunk, GDIT & Carahsoft
Location: Reston, VA
Hosted By: Red Hat, Splunk, GDIT & Carahsoft
Location: Reston, VA
Traditional approaches to information security are reactive and antiquated. In an era where technology is on-demand, we can no longer afford to be reactive, we must revolutionize all security practices while increasing our capabilities.Following on the heels of executive directives and combined ...

Red Hat Virtual Event
Event Date: April 05, 2022
Hosted By: Red Hat, ATARC & Carahsoft
Hosted By: Red Hat, ATARC & Carahsoft
Federal agencies are now required to adopt a Zero Trust architecture and leaders must develop plans to implement the IT tools necessary to meet regulations. Implementing a Zero Trust architecture should strengthen other existing security practices and tools, it doesn’t require a massive acquisition of new ...

Virtual Event
Event Date: March 30, 2022
Hosted By: Cognilytica & Carahsoft
Hosted By: Cognilytica & Carahsoft
Artificial intelligence (AI) and machine learning (ML) systems provide great value in data processing and are playing a central role in decision-making in state and local government agencies.This panel is part of a larger series, the whole of which can be found on our resource hub -

Red Hat Webcast
Event Date: March 29, 2022
Hosted By: Red Hat & Carahsoft
Hosted By: Red Hat & Carahsoft
Security remains a major concern for government agencies as they adopt cloud technologies and develop applications. The Department of Homeland Security (DHS) needs a simple approach to solution delivery that incorporates security into the DevOps lifecycle.During this workshop, Brandon ...

Red Hat LeadGen
Event Date: March 14, 2022
Hosted By: Red Hat, Zettaset & Carahsoft
Hosted By: Red Hat, Zettaset & Carahsoft
Red Hat's Michael Epley, Chief Architect and Security Strategist, and Zettaset's Maksim Yankovskiy, CTO, discuss the absolute need for 21st century data protection to guard sensitive data no matter where the data is processed. The journey and digital transformation to zero trust becomes ...
Resources
Featured
Tune in to listen to Keith Nelson of OpenText talk on stage with Jeff Livingston at the Gov AI Summit in October. In this interview, Keith talks about their recent webinar series, AI for the Rest of Government.
OpenText participated at the Gov AI Summit in October. This video showcases who OpenText is and what OpenText does. Tune in to listen to James Willis, Manager of Solution Consulting, Public Sector, OpenText
Article

Voltage Data Security by OpenText provides advanced encryption and tokenization solutions to safeguard sensitive data across various platforms and environments. It helps organizations achieve regulatory compliance and mitigate data breach risks by ensuring data remains protected throughout its lifec...
SMAX SaaS, the OpenText IT Service Management (ITSM) solution, is now available at moderate impact level for the U.S. Federal Risk and Authorization Management Program (FedRamp®). SMAX helps organizations deliver modern IT services, increase IT productivity, and decrease risks and costs.
Datasheet
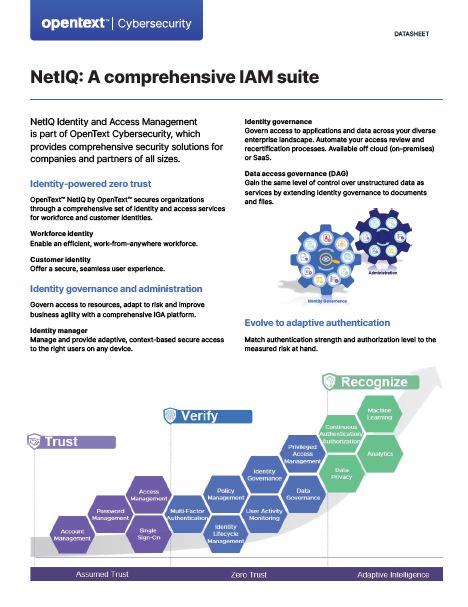
The NetIQ 8.23 datasheet presents OpenText Cybersecurity's extensive identity and access management (IAM) services, featuring adaptive authentication, identity governance, and advanced authentication for workforce and customer identities. Key features include secure access management, policy orc...

Fortify Application Security by OpenText is a comprehensive suite of tools designed to enhance the security of software applications throughout their development lifecycle. It includes features for vulnerability detection, code analysis, and remediation guidance, ensuring robust protection against c...

ArcSight cyDNA by OpenText Cybersecurity revolutionizes cybersecurity with its SaaS-based global signal analytics, unmasking adversarial behavior and providing a bird's eye view of threat actors, ensuring near-time threat analysis and fortified defenses against evolving cyber threats.
Presentation
View Victor Tham’s presentation from our Insider Threat Detection Using AI & ML Webinar. Learn more about the ArcSight, CrowdStrike, and the Insider Threat Landscape.

OpenText IT Operations Management (ITOM) & Cybersecurity solutions not only align flawlessly with DevSecOps principles but also bring forth a unique blend of precision, dedication, and creativity, mirroring the approach we take in crafting the perfect cocktail. Discover the seamless integration of e...
Learn more about how OpenText products can beef up your cyber defenses. From keeping breaches at bay to tightening up your IT system's defenses. OpenText can assist in managing vulnerabilities and exposures across your digital playground.



