Federal government IT staff are tasked with ensuring that the right individual has the right level of access to the right resources at the right time. And while efficient government operations depend on interoperability, historically, security requirements have resulted in silos that hindered that interoperability.
However, it doesn’t need to be this way; opportunities exist for transformation in the government to break down silos, improve operations, and enhance interoperability—without sacrificing security. Below, we’ll review the basics of how to accomplish this by upleveling your infrastructure to employ a Zero Trust approach to authentication.
The Challenge: Fragmented Identity
 The federal government heavily relies upon PKI-based authenticators to verify identity and grant access to resources. However, these authenticators pose several access and security challenges, resulting from the numerous issuing systems and standards.
The federal government heavily relies upon PKI-based authenticators to verify identity and grant access to resources. However, these authenticators pose several access and security challenges, resulting from the numerous issuing systems and standards.
For instance, not all PKI credentials are issued by the same system to support the same level of security—and often, agencies require a mix of PKI and non-PKI credentials. Therefore, employees may need multiple authenticators to access different systems, and agencies must support all of those systems, each introducing its own identity silo.
As a result, many agencies have a fragmented identity landscape, so siloed technologies cannot communicate with each other—the opposite of interoperability.
The Solution: Zero Trust Authentication
Zero Trust is the identity-centric security framework that assumes the network is hostile and users cannot be implicitly trusted. Implementing Zero Trust, which the Executive Order on Improving the Nation’s Cybersecurity mandates for federal agencies, requires continuous authentication and authorization of a user’s identity before granting access to resources.
Federal Identity, Credential, and Access Management (ICAM)—or the set of tools, policies, and systems to enable secure access to information in support of federal business objectives makes this possible.
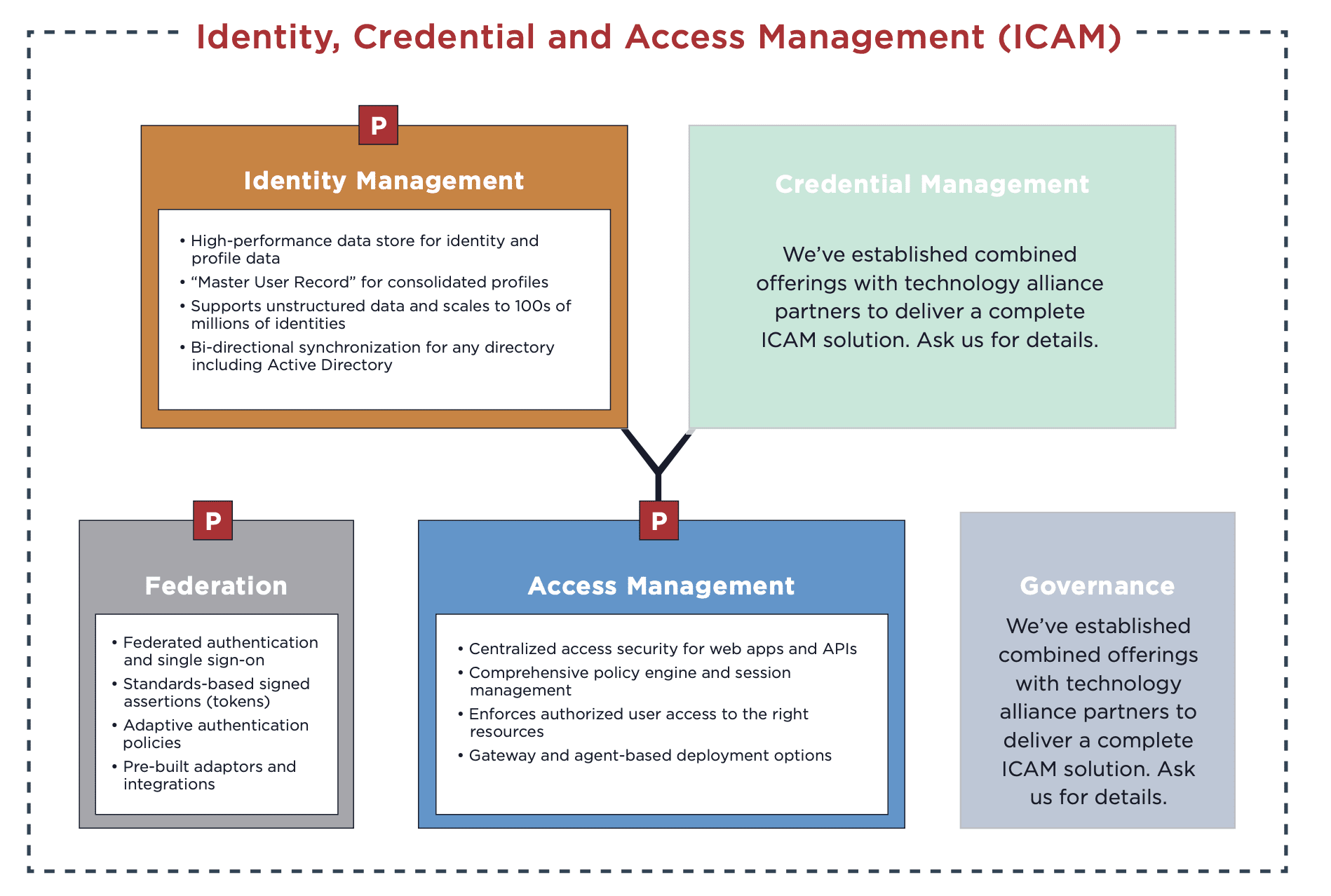
Therefore, you must uplevel the ICAM components supporting those authentication capabilities to implement Zero Trust Authentication. Notably, this doesn’t require ripping and replacing your infrastructure. By employing standards-based technologies, you can augment ICAM capabilities to make the most of existing investments.
Below, we’ll review how to modernize ICAM capabilities and implement Zero Trust Authentication by upleveling three components.
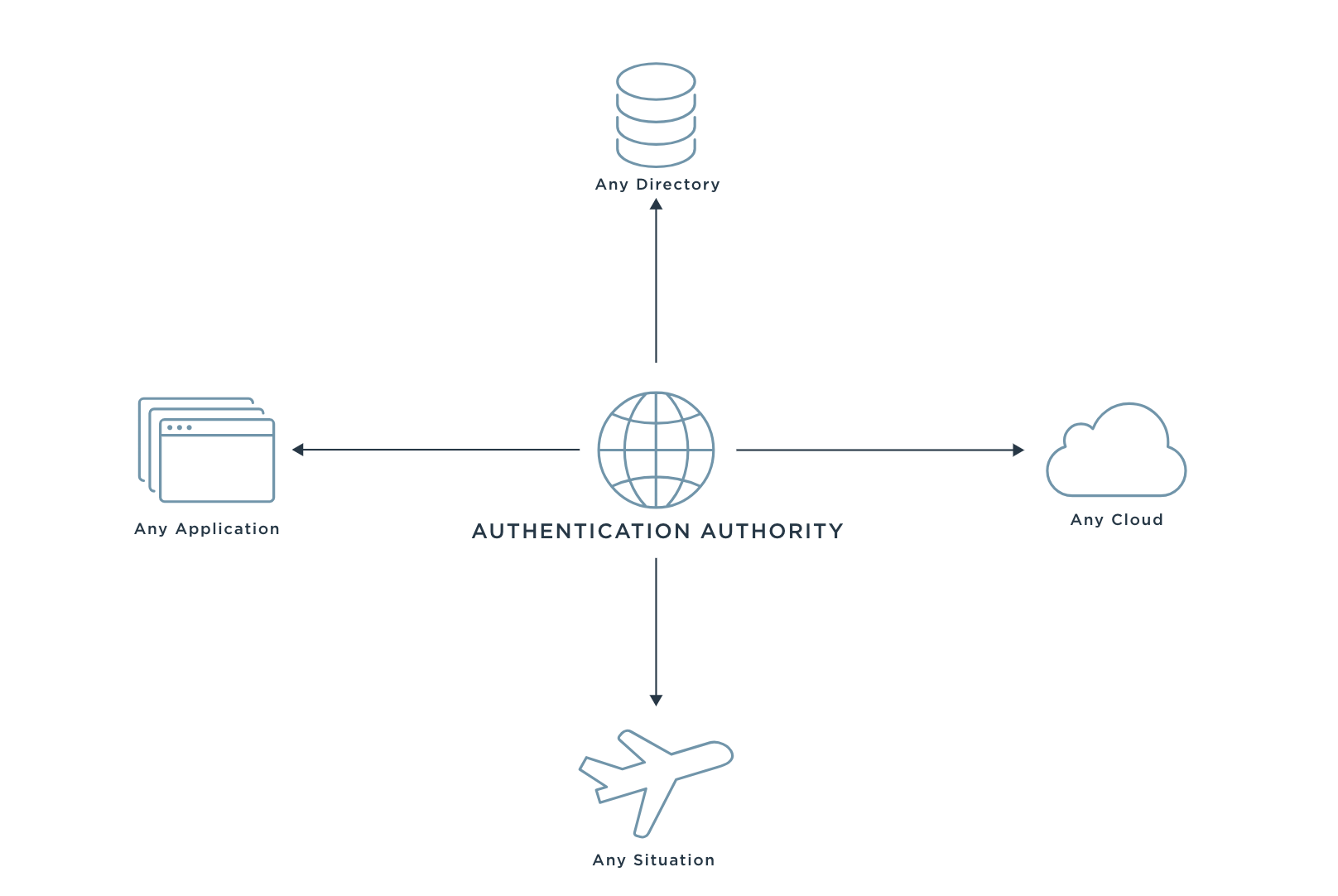
1. Centralized Authentication Authority
The government’s diverse use cases and unique security requirements don’t need to result in fragmentation and identity silos.
Identity federation provides a bridge to connect disparate identities, and a centralized authentication authority allows credentials issued by various systems into a central identity control plane. This breaks down silos by integrating an agency’s PKI authenticators with all of its resources, enabling every individual to securely connect to any resource they need—regardless of location.
2. Dynamic Authorization
Historically, authorization has been a very inflexible process. A user either received access or not based on simple requirements (typically their role in the organization) and metadata (i.e., their attributes). Zero Trust Authentication requires a nuanced approach, which calls for dynamic authorization.
Dynamic authorization takes additional context into consideration to determine if a user should receive initial access to a resource. This includes answers to questions like:
- Does the individual usually access the type of information they’re trying to access now?
- Is the request coming from a trustworthy device?
Considering nuanced information like this enables greater flexibility and control in real-time over what someone can access, transforming authentication from a static to a dynamic process.
3. Continuous Monitoring
Even after a user gains initial access, the answers to the questions above could change. For example, maybe the user received initial access to data when they were using a trusted device, but now they’re attempting to access that same data from an untrusted device. In this case, you may want to revoke some or all of their access until they can provide another authentication factor to verify their identity.
This calls for adaptive access security, which requires continuous monitoring. It allows you to monitor access attempts and changing user attributes to ensure the appropriate level of access is given based on the current access attempt’s level of risk.
The result is an adaptive approach to authentication and authorization—one that operates under the Zero Trust assumption that the user cannot be trusted. It is not enough to verify a user once and then assume they are trusted forever; you must continuously monitor user activity and be able to revoke access post-authorization when needed.
Learn More About Zero Trust Authentication
Zero Trust Authentication helps improve communication between systems, maximize use of PKI authenticators, and make risk-based access decisions. And as you begin looking to support the Executive Order, it is only going to be more important to identify opportunities to uplevel your infrastructure and solutions to facilitate this enhancement.
To learn more about the components discussed and the evolution of identity security in the federal government, watch Zero Trust Authentication: Modern Identity Orchestration for Attribute-Based Access Control.







