News story after news story, cyberattack after cyberattack has demonstrated the rampant presence of ransomware in today’s society taking down all shapes and sizes of companies in both the public and private sectors. By 2026, Gartner predicts that unstructured data storage, which is very susceptible to ransomware, will triple in size, and with that, an inevitable increase in the attack surface. Currently 80% of enterprises’ data is made even more vulnerable by the number of daily users, its distributed nature across devices and servers and overall lack of secure protection.[1]
Experts have arrived at this bottom-line conclusion—everyone is vulnerable to a ransomware attack and cybersecurity measures have become an absolute necessity, not an option.
RANSOMWARE DEFINITION
 Ransomware is a form of extortion through malware exploiting cyber vulnerabilities to infiltrate systems and capture vital operating or private data. The cybercriminals require payment, often in the form of cryptocurrency, for the release, restoration or decryption of the files or the assurance of not blackmailing individuals with the information accessed. Only 2% of organizations within healthcare get their full data back even after paying the ransom, with the majority of organizations receiving about 65% of their information back.[2] Currently, the situation has escalated to the point where bad actors are demanding multiple ransoms, one to restore the data and others to not publish the information on the black market.
Ransomware is a form of extortion through malware exploiting cyber vulnerabilities to infiltrate systems and capture vital operating or private data. The cybercriminals require payment, often in the form of cryptocurrency, for the release, restoration or decryption of the files or the assurance of not blackmailing individuals with the information accessed. Only 2% of organizations within healthcare get their full data back even after paying the ransom, with the majority of organizations receiving about 65% of their information back.[2] Currently, the situation has escalated to the point where bad actors are demanding multiple ransoms, one to restore the data and others to not publish the information on the black market.
The primary four ways ransomware infects a system are through:
- Phishing emails and malicious links
- Insecure network ports, devices and services
- Backdoors left by other malware
- Network vulnerabilities such as poor password hygiene with little user authentication, too many legacy systems, missing software patches and updates etc.[3]
The rise of ransomware as a service (RaaS) has increased the ease of carrying out a cyberattack with practically no technical knowledge necessary for a criminal to execute the attack.[4] One group creates the malware program code and then sells it for other groups to initiate the attack on specific victims.[5] X-Force head Charles Henderson said these crime affiliations have created a condition in which “criminals are more collaborative than the cybersecurity industry.”[6]
All the shifts and advancements in ransomware require a frank review of the past few years and the statistics to understand the situation, properly form the best course of action and minimize the repercussions on American citizens through critical infrastructure.
RANSOMWARE LANDSCAPE
Ransomware has existed since 1989; however, the past two years have seen a dramatic spike in quantity and impact of cyberattacks. All areas of government, business and healthcare are susceptible regardless of their size and relative importance.[7] In recent years, the landscape has changed from individual domestic hackers exploiting opportunities to organized groups of professional criminals based in and often funded by adversarial nations to strategically disrupt critical functions and achieve financial and political goals.[6]
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified 16 major critical sectors whose capabilities directly impact the national public health, safety, security and economy of America, most of which (14 out of 16) have fallen under heavy ransomware attack in the past two years.[8] By targeting these essential infrastructures across financial, industrial, transportation and healthcare institutions, bad actors can disrupt nation-wide and global supply chains. CISA executives stress the importance of universal action to improve cybersecurity and combat the widespread ransomware threat. Because of the interconnectivity of U.S. infrastructure, they warn that if one organization is compromised, cybercriminals could gain access and infiltrate other larger vital service providers and ultimately spread out of control.[9]
Government agencies and critical businesses are not the only groups seeking to improve through tech modernization. The ransomware landscape has changed drastically due to advances in cybercriminal activity as well.
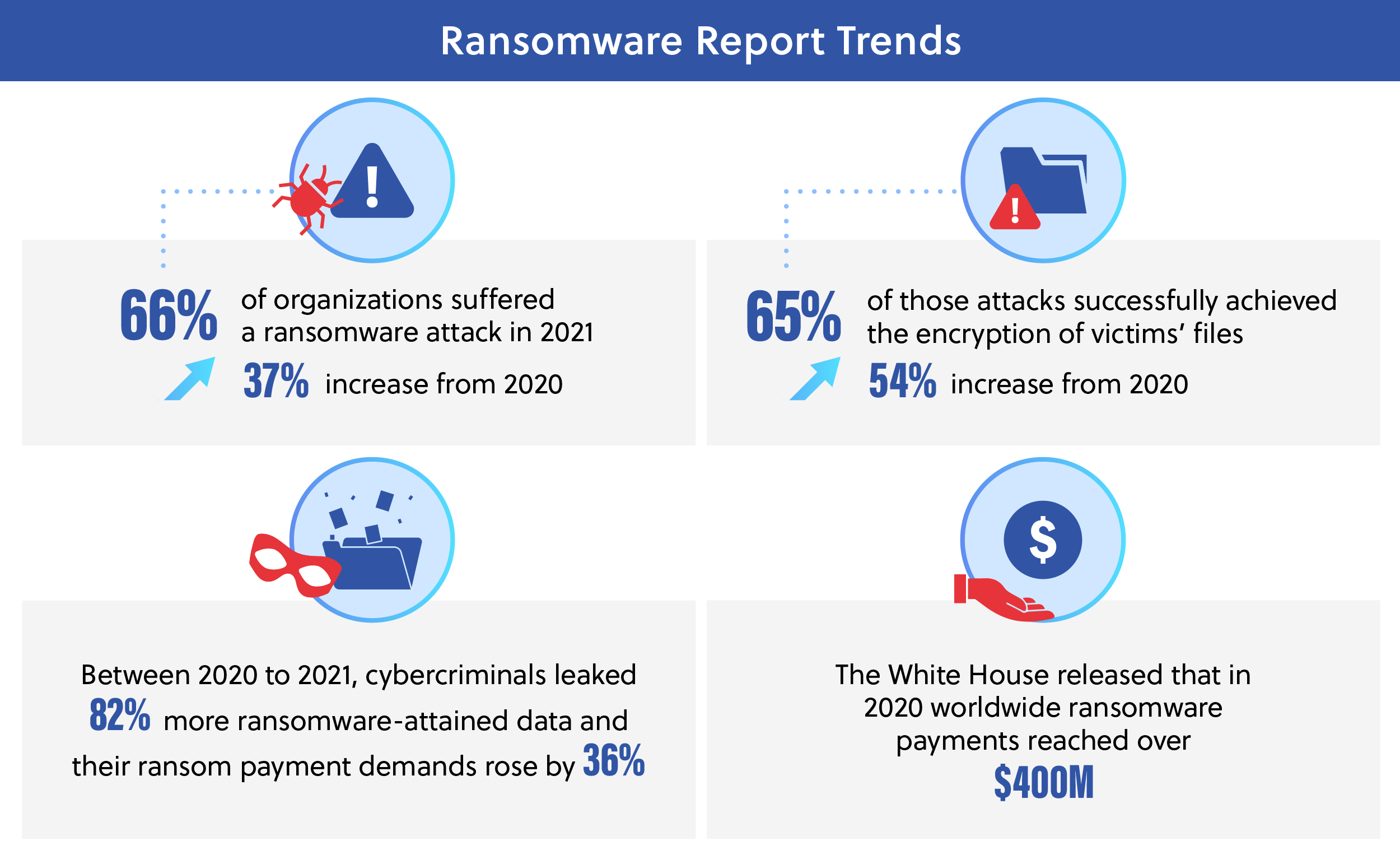
The timeline of these attacks has also accelerated. In 2019, the average time between the initial system infiltration to malware deployment was over two months but in 2021 it dropped 94% to an average of less than four days.[12] Every 10 seconds, a new victim is attacked by ransomware. Not only are attacks and ransom demands increasing and their deployments faster, the majority (60%) of companies do not feel prepared if their company were to be faced with a similar threat in the next 12 months.[13] This problem is expected to continue to grow over the next decade, with ransomware cost predictions of more than $265 billion in total damage by 2031.[14] Agencies and organizations must evaluate their cybersecurity standing and make improvements to ensure that they can withstand these escalating attacks.
RANSOMWARE — ACTION REQUIRED
Contrary to public opinion, most cybercriminals do not primarily target organizations based on the perceived importance of their data, but rather the ease of access to infiltrate the system and the probability that the company will pay the ransom. Critical infrastructure in particular has an obligation to strengthen and reinforce their cybersecurity to prevent disruption and protect these vital functions for the American people. With the increasing trends, officials point to the new harsh reality that ransomware is not a question of if a company will be attacked through malware, but when. Based on the current landscape, organizations must act or risk being swept away by the growing tide of ransomware.
Carahsoft and its partners offer cybersecurity solutions to defend against ransomware and mitigate the risks. Reach out to discover how Carahsoft can make an impact for your organization. Dive deeper into how ransomware is affecting U.S. critical infrastructures such as healthcare and utilities in our Ransomware in Healthcare and Utilities Blog. Find our full Ransomware Series here.
Resources:
[1] “Protect, Detect & Recover: The Three Prongs of a Ransomware Defense Strategy for Your Enterprise Files,” Nasuni, https://media.erepublic.com/document/Whitepaper-_A_Three_Prong_Ransomware_Strategy_-_Nasuni.pdf
[2] “The State of Ransomware in Healthcare 2022,” Sophos, https://news.sophos.com/en-us/2022/06/01/the-state-of-ransomware-in-healthcare-2022/
[3] “Security Primer – Ransomware,” Center for Internet Security, https://www.cisecurity.org/insights/white-papers/security-primer-ransomware
[4] “Ransomware: In the Healthcare Sector,” Center for Internet Security, https://www.cisecurity.org/insights/blog/ransomware-in-the-healthcare-sector
[5] “Health Care Ransomware Strains Have Hospitals in the Crosshairs,” Security Intelligence, https://securityintelligence.com/articles/health-care-ransomware-strains-hospitals-in-crosshairs/
[6] “Ransomware Attacks on Hospitals Have Changed,” AHA Center for Health Innovation, https://www.aha.org/center/cybersecurity-and-risk-advisory-services/ransomware-attacks-hospitals-have-changed
[8] “Critical Infrastructure Sectors,” Cybersecurity & Infrastructure Security Agency, https://www.cisa.gov/critical-infrastructure-sectors
[9] “Ransomware Hackers Will Still Target Smaller Critical Infrastructure, CISA Director Warns,” Nextgov, https://www.nextgov.com/cybersecurity/2022/07/ransomware-hackers-will-still-target-smaller-critical-infrastructure-cisa-director-warns/374953/
[12] “Ransomware in 2022: Evolving threats, slow progress,” TechTarget, https://www.techtarget.com/searchsecurity/news/252522369/Ransomware-Evolving-threats-slow-progress
[13] “Global Data Protection Index 2021,” Dell Technologies, https://www.dell.com/en-us/dt/data-protection/gdpi/index.htm#pdf-overlay=//www.delltechnologies.com/asset/en-us/products/data-protection/industry-market/global-data-protection-index-key-findings.pdf
[14] “Ransomware in the Utilities Sector,” ThirdPartyTrust and BitSight, https://info.thirdpartytrust.com/hubfs/03%20Guides%20and%20Ebooks/ransomware-utilities-bitsight-thirdpartytrust.pdf
Infographic Resources:
[7] “Ransomware Threat March 2022: Special Report” Nextgov, https://www.nextgov.com/assets/ransomware-threat-ngq122/portal/
[10] “Looking Back at the Colonial Pipeline Ransomware Incident,” Government Technology, https://www.govtech.com/blogs/lohrmann-on-cybersecurity/looking-back-at-the-colonial-pipeline-ransomware-incident
[11] “Much to Do About Ransomware: Report Highlights a Path Forward,” Government Technology, https://www.govtech.com/security/much-to-do-about-ransomware-report-highlights-a-path-forward







